Penetration testing
Identify and eliminate threats with a pen test.
Strike Graph’s penetration testing services simulate real-world attacks, enabling you to identify potential threats and secure your systems before it's too late.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!

Penetration testing closes security gaps so you ace your audit.
No more guesswork
Pen testing isn’t required for most security certifications, but it makes your audit prep a lot faster and easier. You’ll receive a prioritized list of recommendations so you can remedy vulnerabilities before your audit.
Get an outside perspective
It’s hard to spot your own weaknesses. Our pen testers have years of hands-on experience throughout the software development lifecycle and can spot weaknesses you might miss.
Strengthen your security year after year
Pen testing is a valuable tool you can employ year after year to ensure your controls and protocols are working.
What is a pen test?
Want to dive deeper into the benefits of pen testing and learn more about how the process works? This informative article covers all your pen test basics.

Here’s how a pen test works
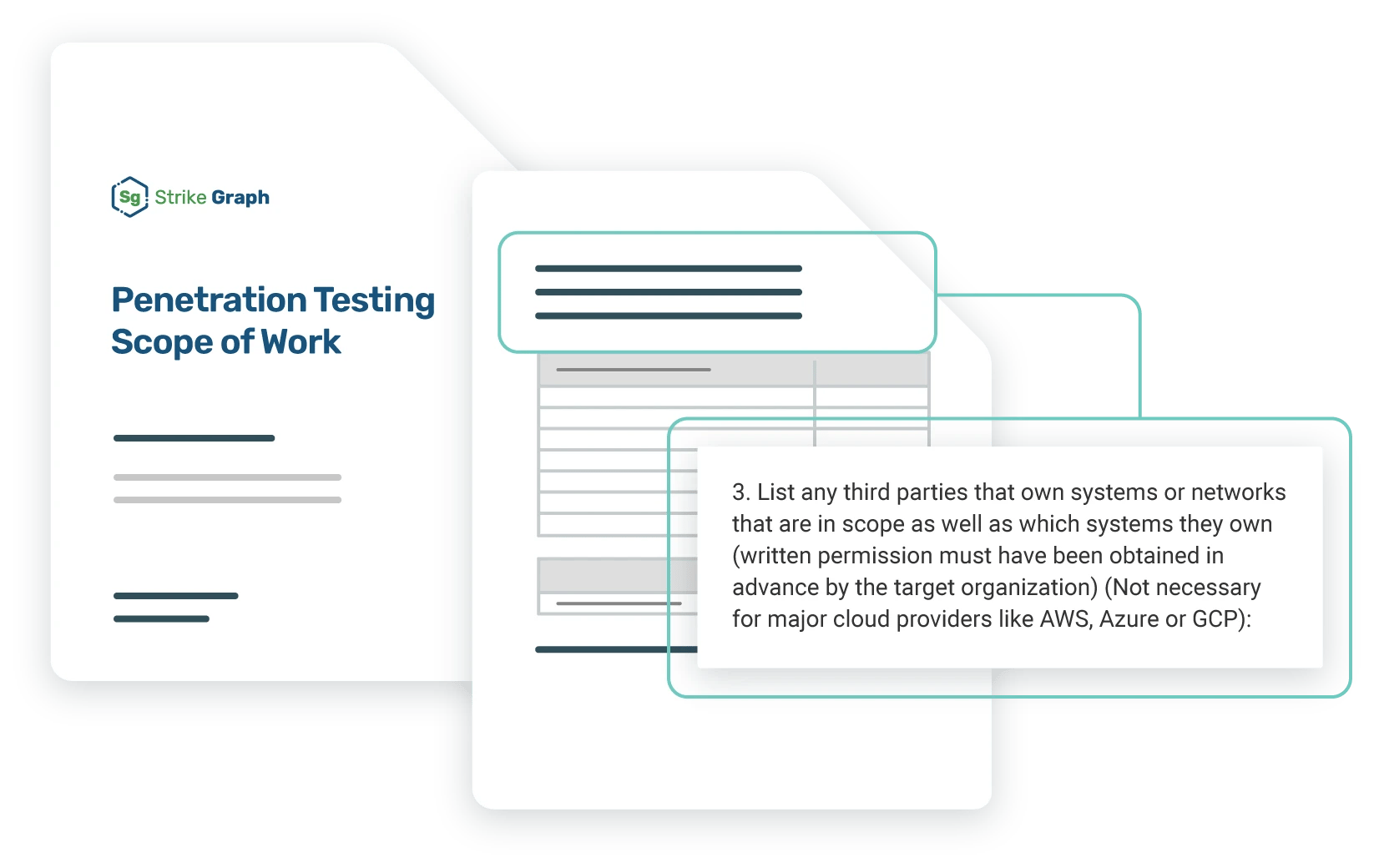
Define your scope
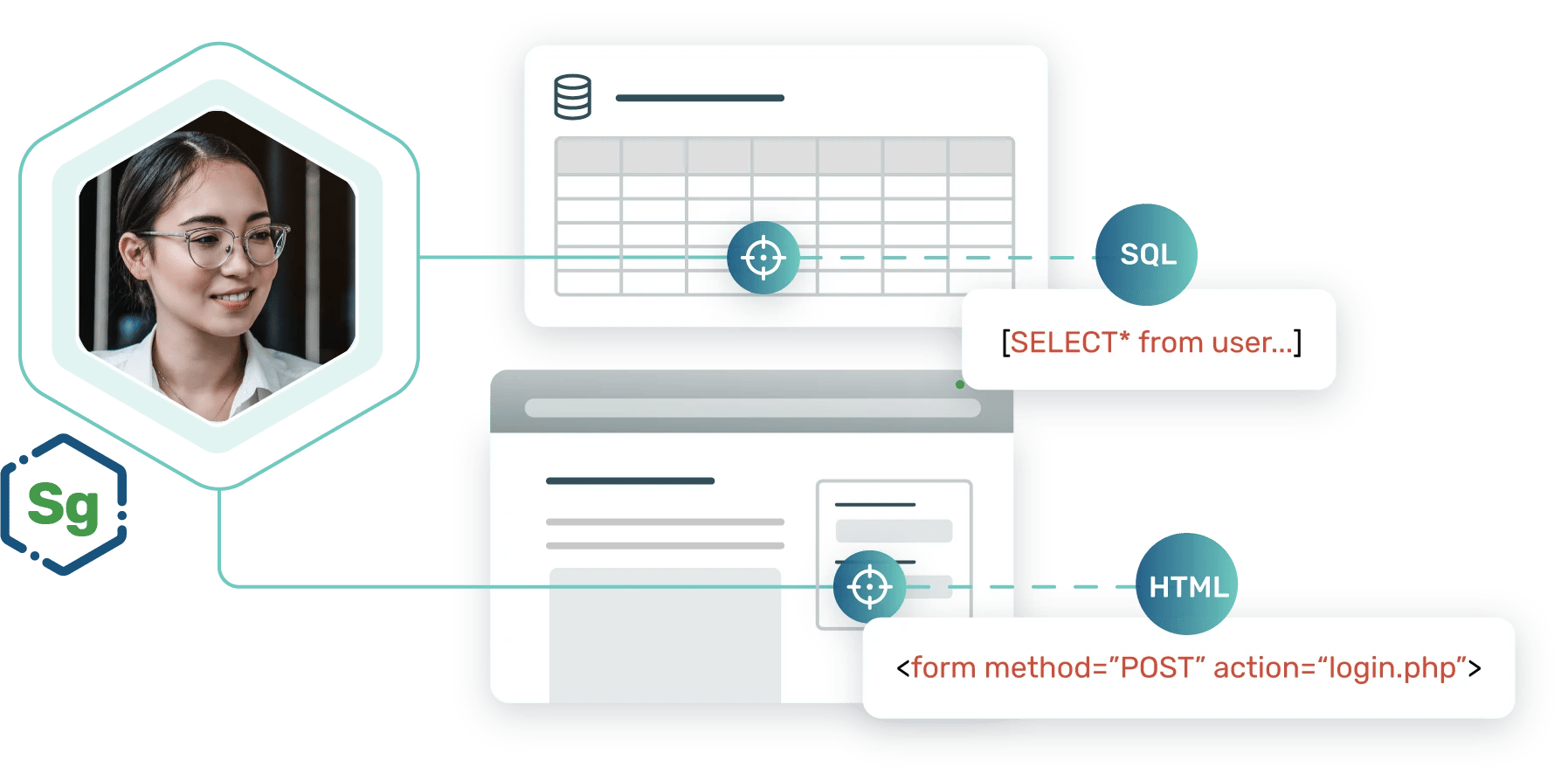
Test your defenses
Get your results
Join the hundreds of companies that rely on Strike Graph for security compliance

Have more detailed questions about penetration testing? We have answers!
What happens during a pen test? Do I need to prepare?
During a pen test, an ethical hacker or pen tester will simulate an attack to enter your system. If successful they will attempt to gain access to the most sensitive information possible and determine how long it takes an internal security team to notice that they are in the network.
To prepare, you need to set the scope of the pen test and provide the pen tester with data about your system. After the pen test, findings will be shared with management and the IT team. Recommendations are prioritized so your team can focus on any critical findings as soon as possible.
How often should a pen test be performed?
A pen test should be performed at least annually or when one of the following occurs:
- The addition of significant change to infrastructure or applications
- The modification of end-user access policies (permissions or roles)
Some organizations with a fairly static environment and code base may only need to test every other year. However, there may be compliance or regulatory factors that require annual testing. Every Strike Graph customer receives an annual pen test as part of their subscription to ensure their security posture is rock solid.
Is a pen test the same as a vulnerability scan? Do I need both?
A pen test simulates an outsider or hacker gaining access to the organization’s environment. The goal is to assess how security is managed within a system. Pen tests utilize a formally repeatable process to infiltrate, exploit and ultimately report on a target.
A vulnerability scan is a subset of pen test activities and is designed to test a network and related systems against a known set of common vulnerabilities. It is typical to run vulnerability scanning at a more frequent cadence than a pen test.
Both result in actionable items, however, a pen test will simulate a ‘live’ threat or attack, whereas vulnerability scans look at the weaknesses already in your system. A well-rounded security program will perform both types of tests.
Does my SOC 2 audit require a pen test?
Penetration testing is not a requirement for SOC 2 compliance. However, it is necessary to ensure that controls are in place to detect and prevent unauthorized access to systems, applications, and data. In addition to a pen test, you may also consider periodic vulnerability scans to address your unique IT risks as this can help further streamline your aduit.
Can’t find the answer you’re looking for? Contact our team!
Additional pen testing resources
Our extensive library of resources will answer all your questions about security compliance.
Ready to revolutionize how you manage security compliance?
Why wait?
Get started for free.
The best way to understand how powerful the Strike Graph platform is is to jump right in and give it a spin.
Still have questions?
Let us show you around.
Schedule a demo, and one of our security experts will show you how Strike Graph can empower you to reach your security goals.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)


