- Frameworks
- CMMC
Achieve CMMC compliance faster
Strike Graph’s AI-powered GRC platform streamlines compliance and enables teams to complete self-assessment, manage POA&Ms, and document SSP —all in one place.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!

Strike Graph takes the headache out of CMMC requirements.
CMMC compliance is critical for organizations working with the Department of Defense (DoD), but navigating the evolving requirements can be complex and time-consuming.
SAVE TIME
The fastest way to get CMMC compliant.
Designed with input from industry experts, Strike Graph simplifies CMMC compliance with self-assessments, POA&M management, automated SSP creation, and easy report exports for auditors. Our platform streamlines evidence collection and maps it to NIST 800-171 controls, giving your team full visibility into compliance progress across the organization.

improve visibility
No more spreadsheets.
Manage compliance across multiple frameworks (like SOC 2, ISO 27001, NIST, 30+ others), products, locations, or subsidiaries in a single platform. Strike Graph’s enterprise content management lets you define common evidence once and instantly distribute updates across your organization, ensuring consistency and saving time.

AUTOMATE
Drive efficiencies with AI and automation.
With AI-powered evidence validation and control monitoring, you can fast-track CMMC readiness. As action items are completed, you can track changes to self-assessment scores and audit readiness, giving you real-time visibility into your compliance posture.

Guide for CMMC implementation
I couldn’t imagine getting CMMC compliant across 90 locations without the Strike Graph platform.
Don’t lose lucrative contracts - Strike Graph gets you CMMC compliant.
The thing about IT security compliance is that when you need it, you need it now. That’s why it’s essential to reach compliance before a big deal depends on it.
TRADITIONAL AUDITING FIRMS
And, when you’re ready to expand to other security frameworks or other locations, you have to start back at square one. Working with consultants provides expert assistance, but when the engagement ends, it can be difficult to maintain continuous compliance.
Key features for CMMC requirements
Strike Graph is designed to adapt to your unique business needs, offering the flexibility and support to quickly achieve your compliance goals as your business grows.
Self-assessment
Evaluate your security posture, identify gaps, and track progress with in-platform guidance, so you can confidently manage action items and stay audit-ready.
POA&Ms
Easily identify, track, and resolve compliance gaps with real-time updates and built-in automation — ensuring timely mitigation and preparation for successful CMMC compliance.
System Security Plans
Automatically generate, update and export SSPs from your compliance data within Strike Graph — ensuring accuracy and readiness for CMMC audits.
Verify AI
Patent-pending Verify AI automates internal audits with AI-powered evidence validation and control monitoring — reducing effort, ensuring compliance, and fast-tracking CMMC compliance.
Secure integrations
Connect your existing tools in minutes with Quick Start integration setup. Built on secure, zero-trust principles, it automates evidence collection while ensuring top security.
Enterprise content management
The only GRC platform with enterprise content management supporting compliance across multiple locations, frameworks, products, or business units. Define evidence once, distribute instantly, and save time.
Does your solution involve building code?
Strike Graph's SBOM Manager helps teams efficiently track and manage software components as part of their compliance program.
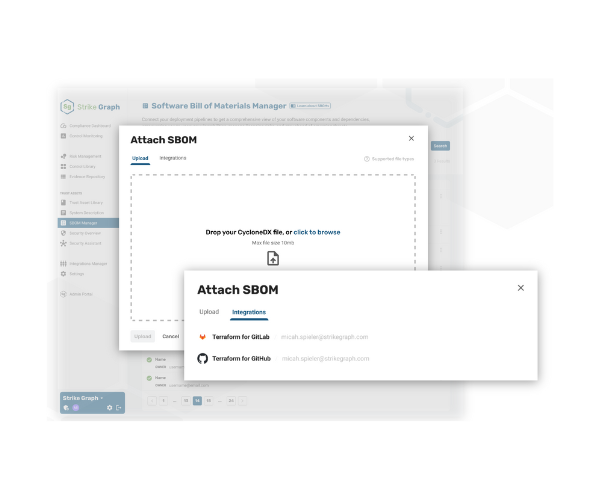
Here’s how it works:
step 1
Identify scope and set up in minutes.
Quickly review the available NIST controls that align with your targeted certification level. For enterprise organizations, set entity-wide controls and tailor them by subsidiary, plant, or location—eliminating unnecessary compliance work while ensuring full coverage.
step 2
Automate, assign, and track effortlessly.
Leverage intelligent automation to assign controls across teams, streamline evidence collection, and complete self-assessments with ease. Strike Graph’s control library and automated workflows simplify risk mitigation while proving the effectiveness of your security program. Complete your self-assessment and track POA&Ms directly in the platform for a seamless compliance process.
step 3
Achieve and maintain compliance.
Effortlessly draft your SSP and track your compliance status in real-time with Strike Graph’s dynamic dashboard. Get instant visibility into your security program, ensuring you achieve and maintain compliance without extra effort—so you're always prepared for audits.
Our customers love that Strike Graph sets them up for success today and in the future
"Strike Graph was the right GRC (Governance, Risk and Compliance) tool we needed at the right time for the right cost."
“Strike Graph makes the compliance process smooth and stress-free. The platform is incredibly intuitive, making it easy to navigate SOC 2, ISO 27001, and other security frameworks without unnecessary complexity.”
“The team at Strike Graph is a guiding light through security land”
Dig into the details
What is CMMC and when does it go into effect?
The Cybersecurity Maturity Model Certification (CMMC) is a framework set by the Department of Defense (DoD) to ensure that contractors and suppliers handling sensitive information meet specific cybersecurity standards. It helps protect federal contract information (FCI) and controlled unclassified information (CUI) within the defense supply chain.
CMMC 2.0 requirements are expected to start appearing in Department of Defense contracts as early as mid-2025, following a phased rollout. Contractors should begin preparing now, as organizations will need certification before they can bid on contracts that include CMMC requirements.
What is the difference between NIST 800-171 and CMMC?
NIST 800-171 is a set of cybersecurity controls focused on protecting FCI and CUI within non-federal systems, which many contractors already follow. CMMC builds on NIST 800-171 by adding verification requirements and multiple maturity levels, which assess not just the presence of controls but also the effectiveness and robustness of cybersecurity practices across organizations.
Who does CMMC apply to?
CMMC applies to all organizations within the DoD supply chain, including contractors, subcontractors, and any business handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) as part of their work with the DoD.
Who does NIST 800-171 apply to?
NIST SP 800-171 provides recommended requirements for protecting the confidentiality of controlled unclassified information, or CUI, for government contractors and subcontractors. Therefore, if an organization is a part of the Department of Defense (DoD), General Services Administration (GSA), National Aeronautics and Space Administration (NASA), or other federal or state agencies’ supply chain, it must implement the security requirements included in NIST SP 800-171.
What are NIST 800-171 controls?
NIST 800-171 has 110 controls organized across 14 control families. These control families include:
- Access control: Determines who has access to data and whether or not they’re authorized
- Audit and accountability: Ensures your staff is adequately trained on the handling of CUI
- Awareness and training: Ensures you know who’s accessing CUI and who’s responsible for what
- Configuration management: Ensures you follow guidelines to maintain secure configurations
- Identification and authentication: Allows you to manage and audit all instances of CUI access
- Incident response: Ensures you prepare a response plan for breaches of CUI data
- Maintenance: Ensures ongoing security and change management in order to safeguard CUI
- Media protection: Secures the handling of external drives, backups, and other backup equipment
- Personnel security: Ensures you train your staff to identify and prevent insider threats
- Physical and environmental protection: Ensures only authorized personnel are in physical spaces where CUI lives
- Risk assessment: Helps you develop a risk profile for CUI breaches as well as evaluate your current level of risk
- Security assessment: Audits and verifies the effectiveness of your security procedures
- System and communications protection: Secures your comms systems and channels
- System and information integrity: Addresses new vulnerabilities and system downtime
Can’t find the answer you’re looking for? Contact our team!
See in real time how Strike Graph simplifies CMMC compliance.
Request a demo below, and one of our security experts will walk you through how our AI-powered platform streamlines CMMC compliance - streamlining self-assessments, POA&M management, SSPs, and more - so you’re always audit-ready.
Additional resources
Read more about NIST 800-171 and CMMC from the Strike Graph experts.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)








