- Frameworks
- ISO 42001
ISO 42001:
Balance AI innovation and governance
Strike Graph simplifies the new ISO 42001 certification, making it quick and easy to deploy. Gain complete control and visibility into your AI security posture and reduce risk to your business. Instill stakeholder confidence by ensuring your AI is managed in accordance with the latest global standards.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!

Be one of the first companies to get a global AI security certification
Strike Graph makes it easy and efficient to get ISO 42001, the first global standard for companies leveraging AI and cutting edge technology.
SAVE TIME
Streamline efforts across multiple frameworks
Prove once, comply with many. If you’ve already done ISO 27001, you’re well on your way to compliance with ISO 42001. For customers looking beyond ISO, the Strike Graph platform can easily leverage existing privacy and information security controls to meet other framework standards.

get support
Leverage expert guidance and guides
Strike Graph offers guides to support as you develop your unique security processes for AIMS - and a successful certification of ISO 42001. Unlike our competitors, we take the time to guide you through and implement a truly robust AIMS. From internal experts to trusted partners, Strike Graph offers resources with deep expertise to help you every step of the way.

cement trust
Demonstrate your commitment to AI security
Trust is crucial when selling, using, and supporting AI products. Leveraging Strike Graph will help you get this certification faster and maintain compliance with global industry standards for AI as it evolves. ISO 42001 requires a risk-based approach, and Strike Graph has this built into the platform so you don't have to start from scratch - you can leverage risk-based tools on day 1 and beyond.
Here’s how it works:
Design
Operate
Measure
Certify
Key features of the Strike Graph platform
The Strike Graph platform was designed to be customized to meet your unique business needs, giving you the flexibility and support to hit the ground running towards your compliance goals.
Extensive template library
Strike Graph offers customizable, audit-tested policy templates and pre-loaded controls designed to fit your AI program's needs. 100% of AIMS policy and procedure templates are pre-built, so you’re ready to hit the ground running.
Customizations
Every organization has unique security needs and risk profiles. With Strike Graph’s platform, you can create a compliance program that addresses your critical security areas, not generic requirements.
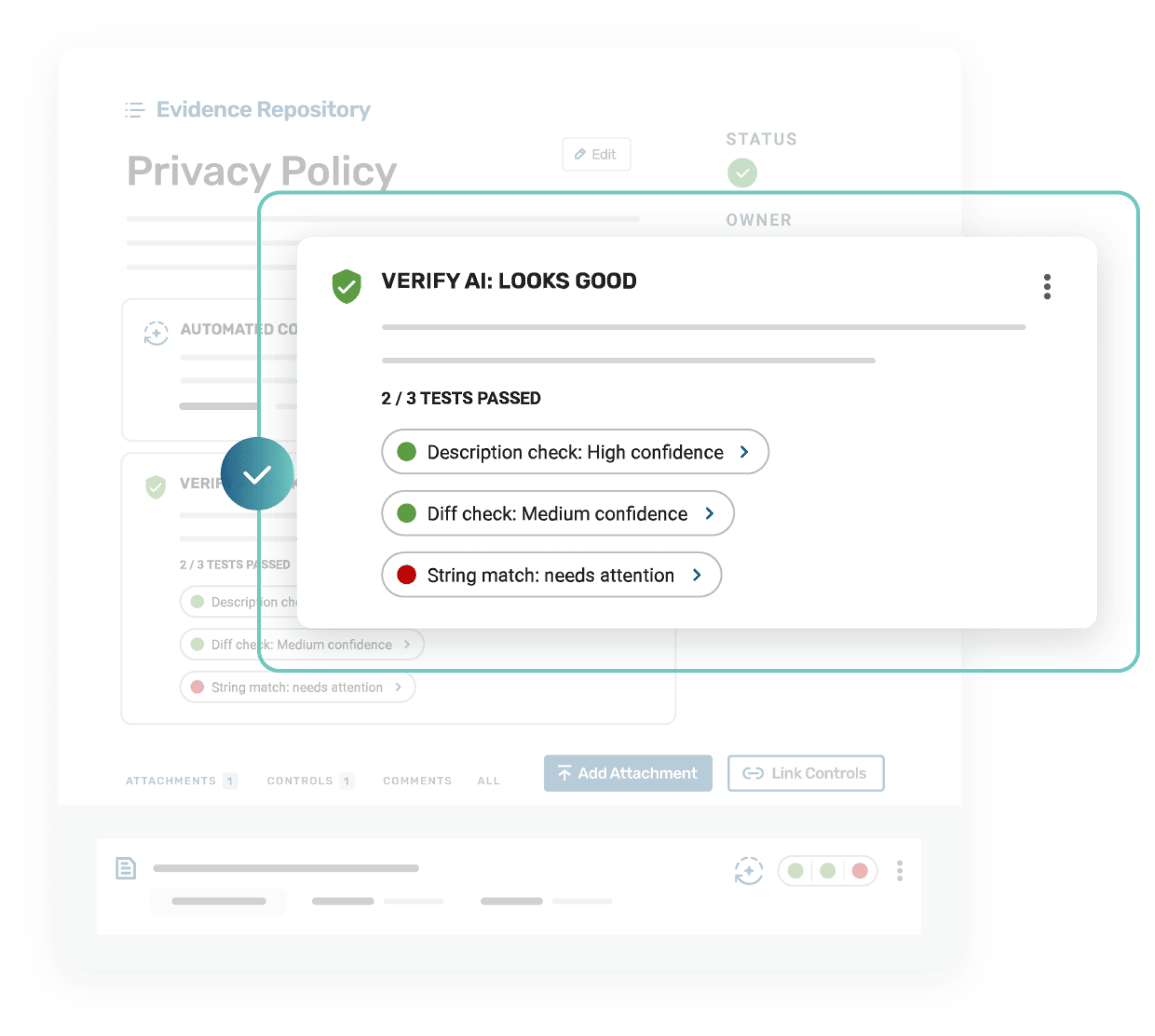
Verify AI
Unique to Strike Graph, leverage Verify AI to confirm whether the documentation you created meets and maintains the ISO 42001 standard.
Gap analysis
Identify discrepancies between your current security posture and desired compliance standards. By pinpointing areas of non-compliance, we equip organizations with the ability to prioritize remediation efforts and allocate resources effectively.
Dashboards & reporting
Strike Graph’s user-friendly dashboards and powerful reporting tools provide visibility into your AI security posture and help build trust with stakeholders. View active risks, monitor control effectiveness, and track evidence status – all in one platform.
Easy integrations
Strike Graph’s low-code integrations give you the flexibility to gather any type of evidence from your existing systems. Businesses can automate evidence collection quickly and easily from over 5,000 data points across their tech stack.
Stop wasting valuable resources
At the most basic level, companies manage risk to avoid regulatory fines and breaking trust with customers and stakeholders. A risk-based approach ensures you’re using precious time and resources only on tasks that actually make your business more secure. Learn how to get started and manage emerging risks to your business.

Highly Recommended
"Their reporting and monitoring features let us keep a close eye on our compliance efforts, spot any hurdles, and measure how far we've come. It's been a real game-changer for managing our compliance projects"
"I have been thrilled with the progress and process of interacting with Strike Graph as a whole"
“The most helpful aspect of Strike Graph is its ability to automate compliance processes and provide clear, actionable insights. It saves our team a significant amount of time and effort, allowing us to focus on other critical tasks. The customer support is also excellent, providing prompt and effective assistance whenever needed."
Let’s unpack commonly asked questions about ISO 42001.
What is ISO 42001?
ISO 42001 is the first global standard for artificial intelligence management systems (AIMS), offering guidance on ethical considerations, transparency, and a risk-based approach to the use and development of AI systems. Designed for those providing or using AI-based products or services, it establishes a framework to manage risks and opportunities, balancing innovation with governance.
Who needs it?
Organizations of any size that are currently using, planning to use, or are developing AI solutions or AI-based products or services should consider implementing ISO 42001. This standard applies to all industries and is relevant to public sector agencies, private sector organizations, and nonprofits.
What is the path to certification?
The path to certification includes annual internal audits and a two-stage external assessment process, resulting in initial certification. In years 2 and 3, a surveillance audit is required to maintain compliance. By year 4, a full recertification audit is conducted to maintain ongoing certification.
Can’t find the answer you’re looking for? Contact our team!
Start your ISO 42001 journey today
Schedule time with our compliance experts to discuss your unique needs and walk through our streamlined ISO 42001 certification process.
Additional ISO 42001 solution resources
Our extensive library of resources will answer all your questions.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)







