Think ISO 27001 is too much to tackle? Think again.
Strike Graph makes ISO 27001 certification simple and fast — and we set you up for easy expansion to other cybersecurity certifications.
Security breaches can have debilitating consequences for your company’s finances and reputation.
Your business partners and customers want to know you have an information security plan — ISO 27001 certification proves that you’re taking every effort to secure sensitive data.
Caught in a web of requirements?
Not sure how to manage cryptography? Never heard of Annex 8.24? Don’t worry — unless you’re an information security expert, you wouldn’t have! That’s why achieving ISO 27001 certification on your own can be tough.
Strike Graph makes
ISO 27001 doable.
Our platform is designed to simplify ISO 27001 requirements and provide you with the guidance and resources you need to quickly and easily achieve compliance.
What is ISO 27001 and why does it matter?
ISO 27001 is an international standard for information security management systems (ISMS), set by the International Organization for Standardization (ISO). It offers a framework for securing and managing information assets. Compliance with ISO 27001 signifies an organization's dedication to systematic risk management and information security. This certification is crucial for entities handling sensitive data, as it assures clients and partners of robust data protection. Achieving ISO 27001 is key in establishing trust and maintaining a competitive edge in today's data-centric business environment.

-min.png?width=2000&height=900&name=Rectangle_20451_20(1)-min.png)
Strike Graph is your roadmap to ISO 27001 certification.
Never feel overwhelmed.
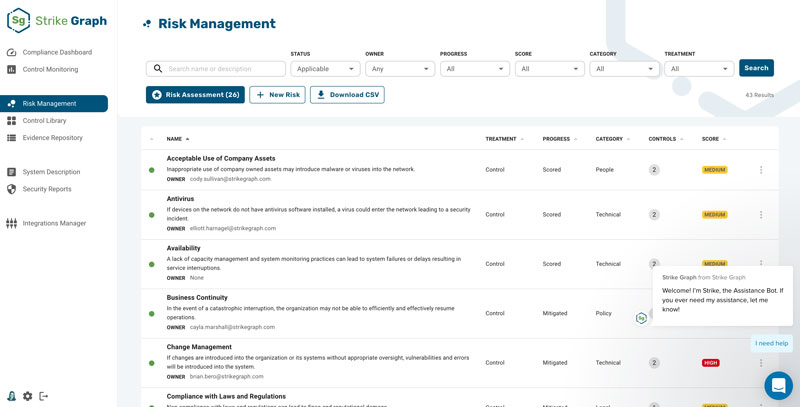
Strike Graph breaks complex ISO 27001 requirements into manageable steps. Everything you need — from progress updates to audit documents — is organized and easily accessible from your dashboard.
Skip ahead with time-saving templates.
ISO 27001 requires a lot of documentation, but there’s no need to produce it from scratch! Our extensive library of policy templates and audit-tested, pre-loaded controls save you hundreds of hours of work.
.webp?width=1184&height=844&name=Policy%20Template%20(1).webp)
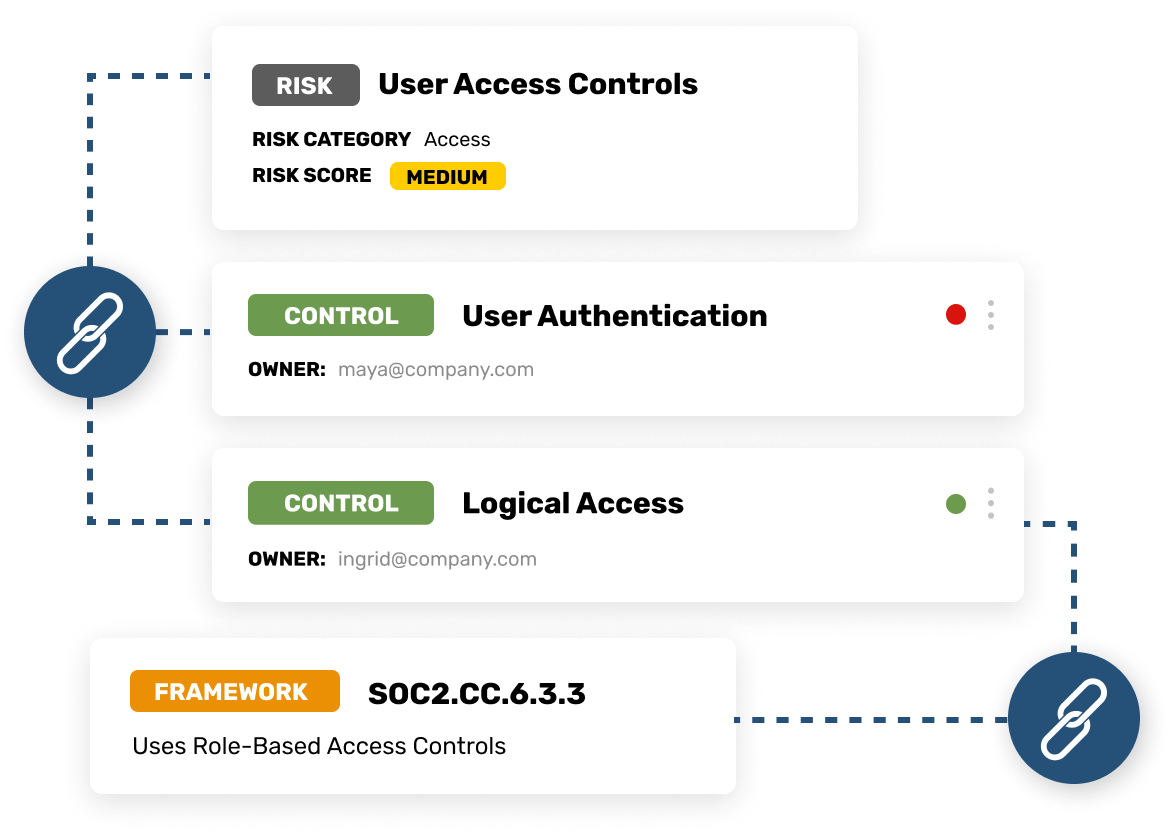
Set yourself up for continued expansion.
Whether HIPAA, SOC 2, or PCI DSS is next on your cybersecurity horizon, Strike Graph’s flexible, cross-certification platform means you can use the work you do for ISO 27001 as a foundation for your next certification.
Packed with
useful features
penetration testing
Design
Operate
Measure
Certify
Check out our reviews





Say goodbye to compliance stress
The team at Strike Graph is very hands-on, making my job a lot easier. From SOC 2 to ISO 27001, compliancy can be confusing, but Strike Graph provides the confidence that I have set my team up for success. Read more on G2.com
— Ben W., partnerships and growth specialist
Strike Graph has quickly become core to our compliance efforts
The platform makes managing your controls and evidence so easy, especially if you have multiple compliance frameworks you're working within (i.e. SOC2, HITRUST, ISO, etc.) Read more on G2.com
— Executive sponsor, information technology and services
Strike Graph is your partner in compliance …
Strike Graph is your one-stop shop to get your security audits going and completed in half the time. There are file repositories for security audits, automated security questionnaires, evidence repository, and great support from the customer success team. Whether you need evidence of HIPAA, SOC2, or ISO, you're in the right place. Read more on G2.com
— Administrator, information technology and services
Find out why hundreds of companies turn to Strike Graph for information security.

ISO 27001: Dig into the details.
Learn about everything ISO 27001 from information security management systems to Annex A.
What is ISO 27001?
ISO 27001 is a framework for an organization’s ISMS, or information security management system. The ISMS establishes a management program designed to address information and data security risks. The standard was originally published jointly by the International Organization for Standardization and the International Electrotechnical Commission in 2005. It was revised in 2013 and again in 2022.
What is an information security management system?
An information security management system (ISMS) is a management program made up of policies and procedures to keep confidential and sensitive information secure. It establishes a systematic approach to security through technologies, policies, procedures, systems, and processes. An ISMS is designed to manage information risks such as data leaks, cyberattacks, hacks, insider threats, or theft. An ISMS enables organizations to secure information in all its forms and increase their resilience to attacks.
An effective ISMS also helps businesses respond to evolving security threats to the confidentiality, integrity, and availability of the data it handles. Businesses can improve cybersecurity culture through an integrated ISMS approach that covers people, processes, and technology. An ISMS enables employees and partners to readily understand risks and embrace security controls in their working practices.
ISO 27001’s focus on information security risk management and continuous improvement makes it the most widely recognized IT Security certification internationally.
Who should get an ISO 27001 Certification?
Any organization that handles confidential or sensitive information and wants to secure that information can benefit from following ISO 27001 requirements. An ISO 27001 certification proves that your company is successfully complying with all aspects of the ISO 27001 framework.
How can my company receive ISO 27001 certification?
An ISO 27001 certification is conducted by an independent third-party assessor. A successful certification audit results in an ISO 27001 certification.
Organizations stay ISO 27001 certified by ensuring their information security management system (ISMS) meets all ISO 27001 requirements. Apart from operating and updating their ISMS, businesses should update documentation and policies to accommodate new products and requirements. Organizations should also conduct periodic risk assessment reviews as risks and threats evolve. In addition to documentation, ISO 27001 requires organizations to perform internal audits of their ISMS, conduct management reviews, and take corrective actions on nonconformities.
Companies can maximize their ISO 27001 certification by investing in training programs for employees who can develop and maintain an ISMS internally. Employees can also become certified as an ISO 27001 Lead Implementer to help their organizations document and implement security-related requirements for ISO 27001 certification.
ISO 27001 certification is valid for three years, after which a company needs recertification. Attaining and maintaining the certification requires organizations to treat information security as a critical business process and to invest resources, effort, and time into ISO 27001 requirements on a year-round basis.
The cost of an ISO 27001 certification traditionally depended on various factors like training, technologies to be implemented and updated, external expertise, and the certification and annual surveillance audits. Strike Graph’s approach puts everything you need within easy reach and tailors the process to your company’s unique risks, cutting the time and cost of ISO 27001 certification.
What are ISO 27001 Annex A Controls?
Purpose
Information security policies
Describe how to handle information security policies
Organization of information security
Provide a framework for information security by defining the internal organization and other information security aspects
Human resource security
Outline the information security aspects of HR
Asset management
Ensure information security assets are identified and responsibilities for their security are designated
Access control
Limit access to information assets based on real business needs
Cryptography
Provide the basis for proper use of encryption solutions to protect the authenticity, confidentiality, and integrity of information
Physical and environmental security
Prevent unauthorized access to physical areas, equipment, and facilities from human or natural intervention
Operations security
Ensure the organization’s IT systems are secure and protected against data loss
Communications security
Protect the network (infrastructure and services) and the information that travels through it
Systems acquisition, development, and maintenance
Ensure that information security is prioritized when purchasing new information systems or upgrading existing ones
Supplier relationships
Ensure that activities outsourced to suppliers/partners use the appropriate Information Security controls and describe how to monitor third-party security performance
Information security incident management
Provide a framework to ensure the proper management and communication of security incidents
Information security aspects of business continuity management
Ensure the continuity of information security management during disruptions as well as information system availability
Compliance
Provide a framework to prevent legal, regulatory, statutory, and contractual breaches and audit whether your implemented information security meets the requirements of the ISO 27001 standard
Can’t find the answer you’re looking for? Contact our team!
Additional resources
Check out more helpful guides from the Strike Graph team!


Additional resources
Check out more helpful guides from the Strike Graph team!
Have more questions?
Contact us using the form below, and we’ll be happy to walk you through our streamlined ISO 27001 certification process in more detail.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)



