A step-by-step implementation guide for CMMC
This guide provides clear, actionable steps to achieve compliance based on your required certification level for Cybersecurity Maturity Model Certification (CMMC) in order to continue doing business with the Department of Defense (DoD) and win future contracts.

Your free CMMC Implementation Guide
Determine and understand your CMMC level requirements
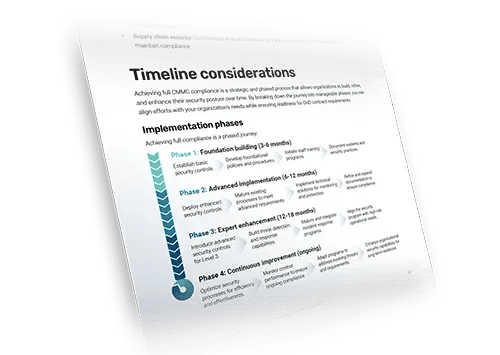
This foundational step ensures that you’re targeting the right security requirements based on the sensitivity of the information you handle and the specific needs of your contracts. This guide provides a step-by-step process for determining your CMMC level and the requirements you must meet for your level.
Foundational
Basic safeguarding practices to protect Federal Contract Information (FCI) with self-assessment requirements.
Advanced
Advanced safeguarding in full compliance with NIST 800-171 controls to protect Controlled Unclassified Information (CUI).
Expert
Adds advanced security measures from NIST 800-172 to combat advanced persistent threats (APTs) and mandates third-party certification.

Cybersecurity Maturity Model Certification (CMMC) is a necessity
Contractors who work with the Department of Defense (DoD) are required to implement CMMC to continue doing business and win future contracts. Get clear, actionable steps to achieve compliance based on your required certification level.
Strike Graph gets you certified fast.
Forget traditional auditing firms. Strike Graph takes you all the way to certification faster and more affordably than traditional solutions.
STEP 1
Design
Assess risk and design a strong security program that fits your business with Strike Graph’s extensive repository of policy templates, audit-tested controls, and educational articles.
STEP 2
Operate
Use the compliance dashboard to distribute ownership of risks, security controls, and evidence automation across the whole team, ensuring your organization meets its security contributions efficiently and effectively.
STEP 3
Measure
Easily measure and monitor the status of your controls so you’re always in compliance and ready for audit.
STEP 4
Certify
Give your partners and customers confidence you’re operating in compliance with all relevant regulations and industry-standard security frameworks with a Strike Graph compliance report.
Strike Graph:
CMMC compliance without the headache
Self-assessment
Evaluate your security posture, identify gaps, and track progress with in-platform guidance, so you can confidently manage action items and stay audit-ready.
POA&Ms
Easily identify, track, and resolve compliance gaps with real-time updates and built-in automation — ensuring timely mitigation and preparation for successful CMMC compliance.
System Security Plans
Automatically generate, update and export SSPs from your compliance data within Strike Graph — ensuring accuracy and readiness for CMMC audits.
Verify AI
Patent-pending Verify AI automates internal audits with AI-powered evidence validation and control monitoring — reducing effort, ensuring compliance, and fast-tracking CMMC compliance.
Secure integrations
Connect your existing tools in minutes with Quick Start integration setup. Built on secure, zero-trust principles, it automates evidence collection while ensuring top security.
Enterprise content management
The only GRC platform with enterprise content management supporting compliance across multiple locations, frameworks, products, or business units. Define evidence once, distribute instantly, and save time.
Trusted by hundreds of fast-growing companies
hs.png)
.png)
.png)

.png)

Trust Operations
Revenue isn’t built on a single certification. It’s the product of a centralized, transparent approach to security and privacy that shows your stakeholders and customers they can trust you. Strike Graph is the platform that makes it possible.

Design
Assess risk and design a strong security program that fits your business with Strike Graph’s extensive repository of policy templates, audit-tested controls, and educational articles.

Operate
Use the compliance dashboard to distribute ownership of risks, security controls, and evidence automation across the whole team, ensuring your organization meets its security contributions efficiently and effectively.

Measure
Easily measure and monitor the status of your controls so you’re always in compliance and ready for audit.
Get the latest updates on security compliance
Enter your email and we’ll send you useful resources to help you on your compliance journey.
