- Frameworks
- CIS
Build a resilient security strategy with CIS Controls
With Strike Graph’s simple and customized approach, you’ll adopt the latest version of the CIS Controls in no time. Show your stakeholders that you take security seriously by implementing this top industry standard. Protect your systems by getting clear visibility into your cybersecurity landscape and reinforcing your defenses against potential attacks.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Strike Graph’s platform makes CIS Controls implementation easy and fast.
Say goodbye to generic compliance checklists. Strike Graph customizes the compliance process, ensuring you focus only on the CIS Controls that matter to your organization.
One investment, ongoing returns
Traditional methods to meet CIS Controls adoption require a lot of one-time effort. You invest significant time and resources to implement the safeguards, and then it’s over. With Strike Graph, the controls and documentation you create during the CIS implementation process make it easy to stay compliant and can be reused for future cybersecurity certifications. For instance, after implementing the CIS Controls, SOC 2 would be nearly 70% complete.

Leverage automation to lighten the load
No one likes chasing down colleagues for documentation. Strike Graph takes care of that for you. Simply assign tasks to the right team members in your organization, then our platform can be configured to automate the collection of CIS evidence. We can also send maintenance reminders, helping everyone stay on top of ongoing compliance.
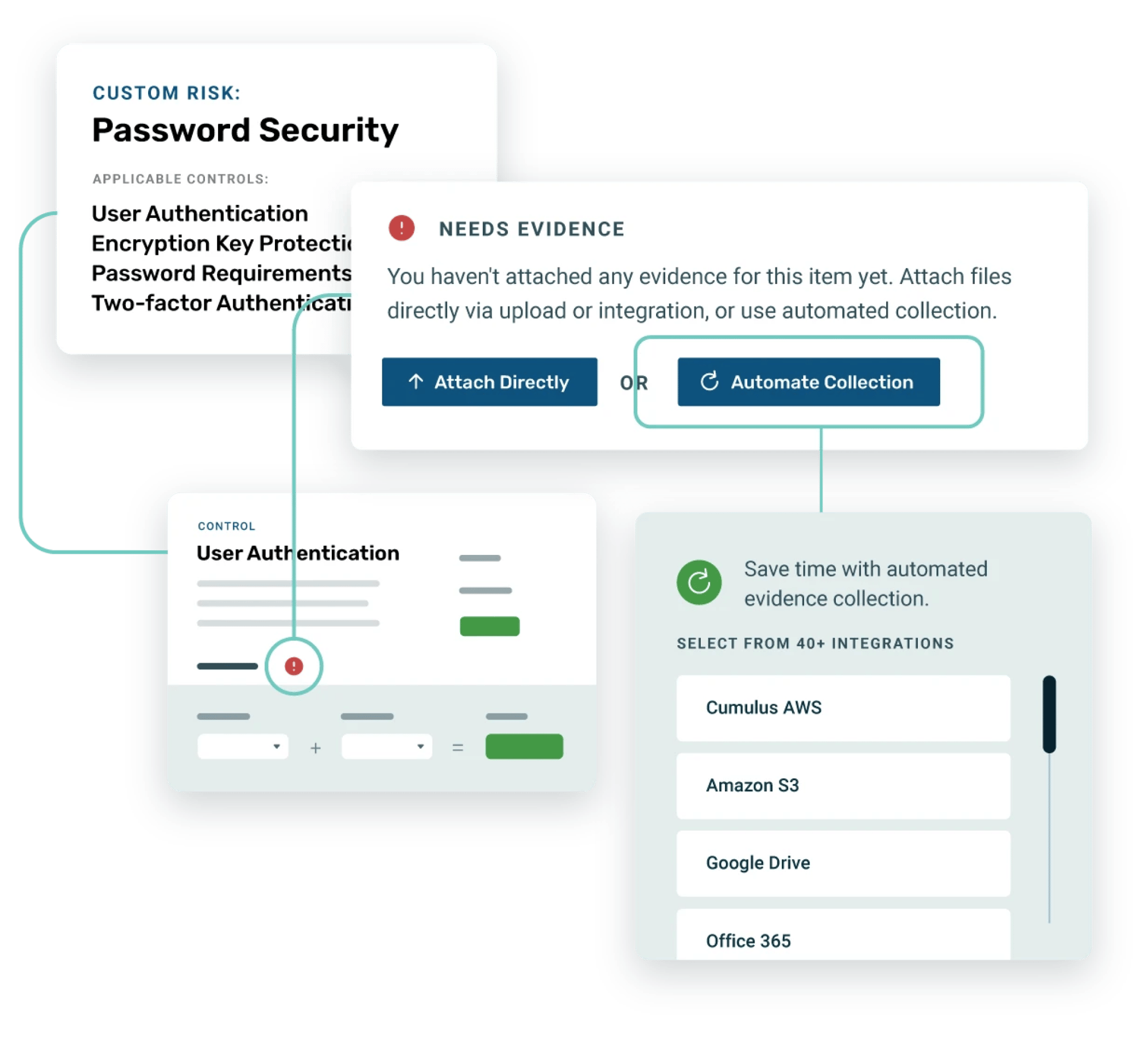
Expert guidance and guides
From internal experts to customizable templates, Strike Graph offers expert resources to help you every step of the way. Unlike our competitors, we take the time to guide you through your IT compliance journey, whether this is your first framework implementation or one of many.

How it works:
See how Strike Graph helps you comply with CIS Controls in 3 simple steps.
Design
Operate
Certify
Key features of the Strike Graph platform
The Strike Graph platform was designed to adapt to your unique business needs, offering the flexibility and support to quickly achieve your compliance goals as your business grows.
Customizations
GRC solutions should work for you, not against you. Develop a compliance program that focuses on your distinct security needs and risk profiles.
Cross-Framework Support
Easily map existing controls and information security practices from CIS to other compliance frameworks and standards, like SOC 2 or ISO 27001.
Extensive Template Library
With customizable, audit-ready policy templates and pre-loaded controls, we help you to quickly implement cybersecurity practices in line with the CIS best practices.
GAP Analysis
Identify gaps between your current security posture and the CIS Controls you’re aiming to meet, enabling you to prioritize remediation efforts and resource allocation.
Verify AI
Strike Graph’s proprietary AI solution, Verify AI, can be leveraged to help confirm whether the documentation you created meets and maintains the CIS Control standards.
Dashboards & Reporting
Get clear insights into your cybersecurity posture, track risks, monitor controls, and build trust with stakeholders —all within a single platform.
The power of AI technology
Outdated checklist approaches to security compliance waste time on tasks that aren't pertinent to your business. A risk-based approach focuses your resources where they actually make a difference.
Highly Recommended
"The resources and templates available within the platform were invaluable. They saved us time, and gave us confidence that the documentation we provided using the templates met the requirements. When we needed just-in-time clarification, we got quick answers to our questions from the Strike Graph team who made themselves available via the online chat."
"The most helpful aspect of Strike Graph is its ability to automate compliance processes and provide clear, actionable insights. It saves our team a significant amount of time and effort, allowing us to focus on other critical tasks. The customer support is also excellent, providing prompt and effective assistance whenever needed."
Smooth journey through compliance and risk management
"Strike Graph platform with its user-friendly interface and comprehensive support resources makes it easier for our company to navigate the intricacies of compliance and focus on our core business operations, moreover, it significantly reduces the time and effort required for compliance activities. Our manager did a great job and addressed all the questions that we had in a timely manner.Review collected by and hosted on G2.com.
FAQs about CIS Controls
What is CIS?
- The CIS Critical Security Controls (CIS Controls) are a prioritized collection of safeguards designed to reduce the most common cyber threats targeting systems and networks. They align with and are referenced by various legal, regulatory, and policy frameworks.
Who needs it?
- Organizations of any size (or budget) that are looking to enhance their cybersecurity posture, protect sensitive data, comply with regulations, and effectively mitigate risks can benefit from implementing the CIS Controls, an industry-accepted security framework.
What is the path to implementation?
The path to CIS Controls adoption starts with reviewing the 18 CIS Controls and conducting a gap analysis to identify areas for improvement. Next, develop a compliance strategy and implement the necessary controls, ensuring to document evidence of your efforts. Perform a self-assessment to verify alignment with the controls and address any findings. Finally, continuously monitor your security measures to maintain compliance.
What are the main differences between the CIS Controls and SOC 2?
While they are both industry-accepted security frameworks and do have overlap, there are several key differences. CIS provides a set of 18 best practices (CIS Controls) that any organization can implement to help their cybersecurity posture, and does not require a formal certification. By contrast, SOC 2 focuses on auditing the internal controls of service organizations in regards to managing customer data securely and is primarily relevant for service providers. SOC 2 also requires a formal audit conducted by a certified public accountant (CPA), which results in a detailed report assessing the effectiveness of the organization's controls.
With Strike Graph, an organization can easily implement SOC 2 after CIS if they need to in the future.
Can’t find the answer you’re looking for? Contact our team!
Begin your journey to CIS Implementation today
Schedule time with one of our compliance experts to discuss your unique needs and walk through our streamlined CIS Controls solution in the Strike Graph platform.
Additional compliance resources
Our extensive library of resources will answer all your questions.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)







