Do you feel like you’re behind in the security compliance game? Are your competitors outpacing you? Even the fastest security certification doesn’t happen overnight, so what can you do in the meantime?
Strike Graph’s security overview proves to potential customers that you have robust security processes — whether you’re between security audits or are working toward initial certification.

The power of real-time security reporting
In a world where data breaches are more common than we'd like, it’s crucial for companies to show they’re not just sitting back prior to their first certification or between external audits. Real-time security reports act like a continuous stream of proof that a company is actively guarding data. It's about building trust.
Real-time reports, like Strike Graph’s security overview, send a clear message to customers and stakeholders: “We’re always on guard.” This isn’t just good for peace of mind; it’s essential for maintaining a strong, trustworthy brand.
But here’s the other big deal about these reports: they’re not just a security blanket for customers, they're a strategic tool for businesses.
Data security isn’t static; it’s a rapidly shifting battlefield. By keeping an eye on security all the time, companies can quickly pivot to tackle new threats as they emerge, staying one step ahead. This isn’t just about dodging threats; it’s about ensuring compliance with the ever-evolving landscape of regulations.
Continuous security reporting means a business isn’t just reacting to issues; it’s proactively managing its security posture. This level of vigilance is key, not only for protecting data but also for ensuring the company meets its legal and ethical responsibilities. In essence, real-time security reports are the heartbeat of a robust security and privacy program, keeping everything in check and everyone informed.
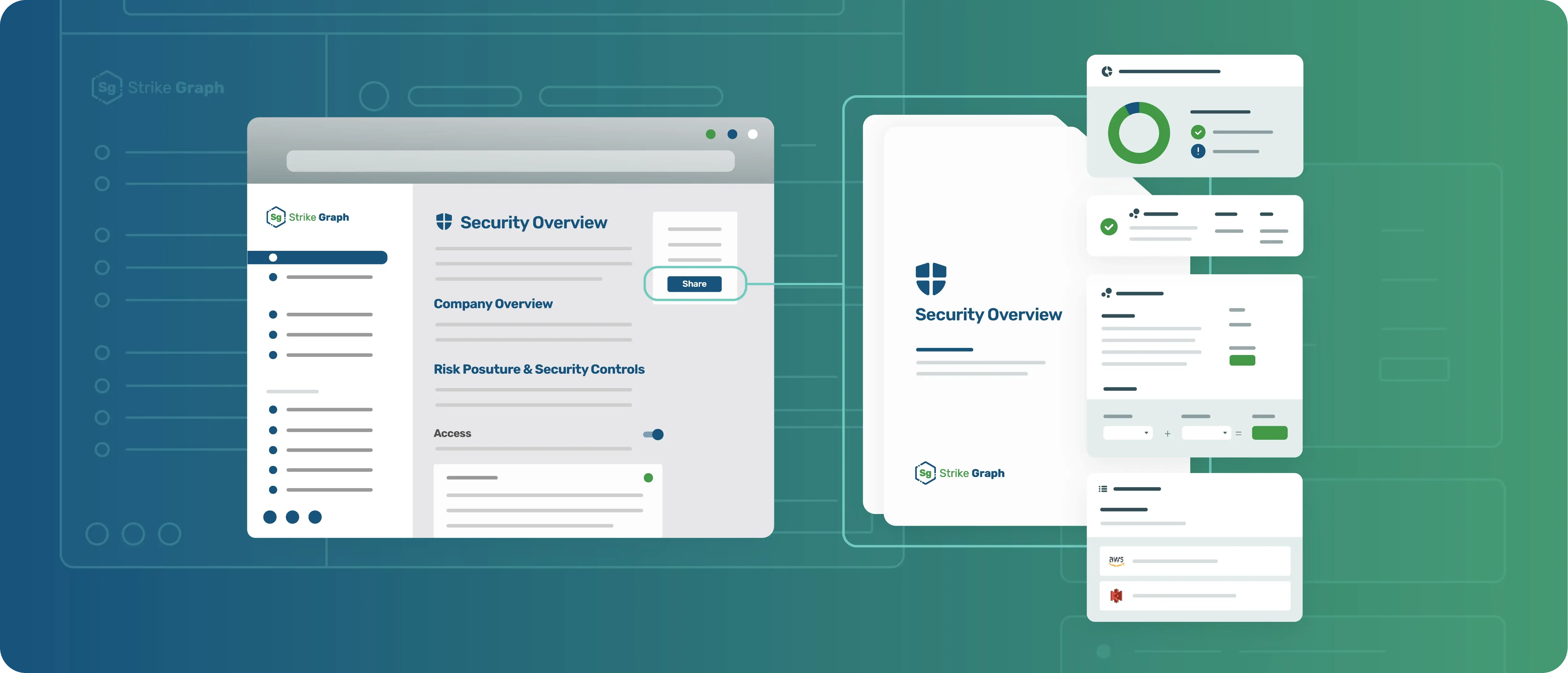
What is the Strike Graph security overview exactly?
Strike Graph’s security overview provides real-time transparency into your security program so that potential customers know they can trust you with their data. The report includes key components and status indicators that show you’re effectively monitoring and mitigating risk:
- Overview: A brief overview of your company and description of your product or service
- Security and risk posture: Includes your company’s unique risk descriptions and a list of your active and in-place controls that mitigate those risks
- Control details: Describes the controls you’ve implemented that cover criteria of your target security framework(s)
Real-time trust building
The Strike Graph security overview provides a snapshot of your data security measures at that exact moment, including the unique risks you’ve identified as pertinent to your business, the controls you’ve implemented to mitigate them, and the connection between those controls and the security framework(s) you’re targeting. This makes it a powerful supplement to your existing security certifications as well as proof of data security and privacy as you work toward an initial certification.
Customizable reporting
Strike Graph’s security overview is customizable so you can provide each client or potential client exactly the security information they’re interested in — even before earning your audit certificate.

The overview section of the report is fully customizable. Introduce your company, its history, and mission statement, who you serve, and a summary of your most relevant products, services, and/or key features. You may also want to consider adding key points of contact within your organization when it comes to compliance and security matters so that your prospective customer knows who to contact to seek out for more information.

You also have full control over which risk categories and controls are shown in the report, letting you share visibility into your entire security program or limit the scope of the report to information appropriate for a particular audience.
Automated for speed
Reporting can be a huge resource drain. That’s our security overview takes care of the grunt work for you. The report pulls in details of your security program automatically, including identified risks and active controls, as well as details of how those controls map to your target framework(s).

Export is quick and simple. After you’ve reviewed the relevant controls and tailored the information you want included in the security overview, one click generates a PDF that can be shared with potential customers directly or via the trust asset library.

Close deals now and build trust for future success
Certifications will always be your most powerful trust asset, but they’re not enough on their own. You need to be able to prove continuous compliance, both before and after you achieve certification. Strike Graph’s quick, customizable security overview is the flexible trust asset you need to land new customers and build long-term brand loyalty.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)