When it comes to security compliance, let's face it: no one enjoys wading through endless checklists that don’t always apply to their business. It's like going to a mechanic who insists on checking parts your car doesn’t even have. That's why at Strike Graph, we advocate a smarter way – a risk-based approach to compliance. Think of it as having a mechanic who only fixes what your car needs, saving you time and money.
What’s great about this approach? It zeroes in on what matters to your business, ditching the one-size-fits-all checklist for a tailored strategy. And, Strike Graph’s in-platform risk assessment makes this shift seamless.
With us, you’re not just ticking boxes — you’re strategically safeguarding your business against real risks, and building a robust security or TrustOps program without the headache.
Checklists bog down your security program
Let's face it, the traditional checklist approach to security compliance is pretty much a relic now. Why? Because it's like trying to catch up with a high-speed train on a bicycle. The world of InfoSec and privacy threats is constantly evolving, with new attack methods and sophisticated techniques popping up all the time. A static checklist just can't keep pace with these advancements.
And here's another thing: security needs aren't one-size-fits-all. Different organizations, especially across various industries, face unique risks. A general checklist might tick some basic boxes, but it won't get into the nitty-gritty of what your specific organization needs to watch out for. And, it will waste a lot of your time on security actions that aren’t pertinent to your business context.
Also, let's not forget that just because you're compliant, doesn't mean you're completely secure. Checklists are often more about ticking off compliance requirements and less about the bigger security picture. Modern cybersecurity (think TrustOps) should be about being a step ahead, focusing on proactive detection and responding swiftly to incidents – areas where checklists often fall short.
So, while a checklist might seem like an easy route, it's not really saving you time or resources in the long run. But don’t worry, there’s a better way.

Why a risk-based approach is better
Modern cybersecurity strategies should be context-specific, incorporate continuous monitoring, threat intelligence, user education, and adaptive response mechanisms, which all go beyond the scope of traditional checklist approaches. Enter a risk-based approach to compliance, which is faster, more efficient, and more effective.
Why? Because it provides a more strategic, flexible, and effective way for organizations to manage their security. By focusing on the specific risks that matter most, organizations can proactively protect their assets, respond to emerging threats, and comply with regulations in a way that genuinely enhances their customer trust.
Here’s a closer look at some of these top benefits of a risk-based security approach:
Tailored solutions
A risk-based approach allows organizations to tailor their security measures according to their specific risks and vulnerabilities. It recognizes that different organizations face different threats and have varying levels of tolerance for risk. Therefore, rather than just meeting generic compliance standards, a risk-based approach ensures that compliance efforts are aligned with the most significant risks faced by the organization.
Efficient resource allocation
By identifying and prioritizing risks, organizations can allocate their resources — both financial, human, and technological — more efficiently. High-risk areas can receive more attention and resources, ensuring a more effective use of the organization’s available budget and expertise. A risk-based approach also enables organizations to adapt their security measures in response to new and emerging threats, ensuring that security strategies remain effective over time.
Continuous improvement
Risk assessments are not one-time events; they are ongoing processes. Regular risk assessments create a feedback loop, allowing organizations to learn from security incidents and near-misses, continually improving their security posture. This also allows decision-makers to have a clearer understanding of the risks involved, helping them make better strategic decisions regarding security investments, policy development, and incident response planning.
Ultimately, a risk-based approach encourages organizations to consider security holistically, encompassing not only technical measures but also human factors, processes, and external dependencies. This comprehensive view leads to a more resilient security posture overall.
Introducing Strike Graph’s risk assessment
Strike Graph's risk assessment feature is part of our comprehensive risk-based approach to compliance that makes it easy to tailor your security program to your unique business vulnerabilities so you don't waste time on unnecessary security tasks.
Here are some of the biggest benefits of using this new feature.
Assign a risk rating
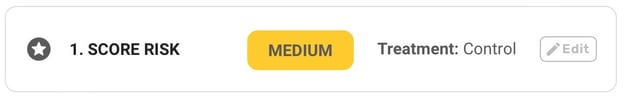
Score for both likelihood and impact — low, medium, or high — to better assess what you and your team need to be prioritizing. The color coding also allows you to easily identify risks that can jeopardize your business at a glance.
Add an owner
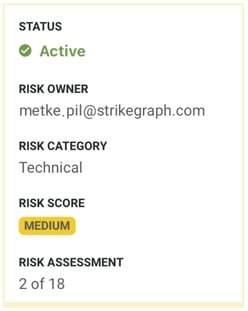
Distribute responsibility across your organization by assigning a team member to each risk. This not only allows everyone to exercise responsibility in regards to your organization’s overall security posture but ensures that no one person is overloaded with owning all aspects of it.
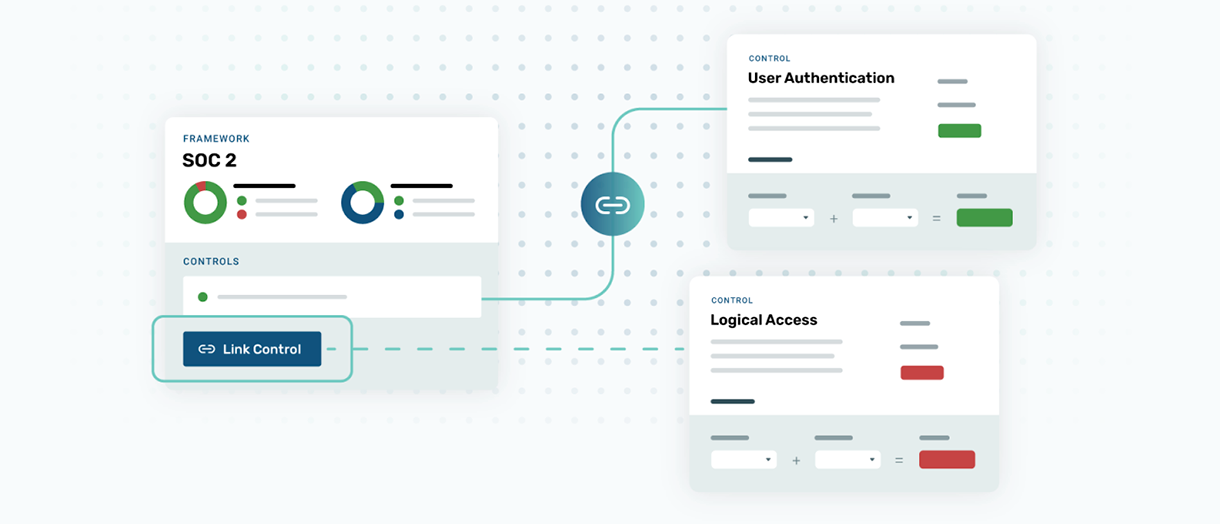
Link pre-mapped controls
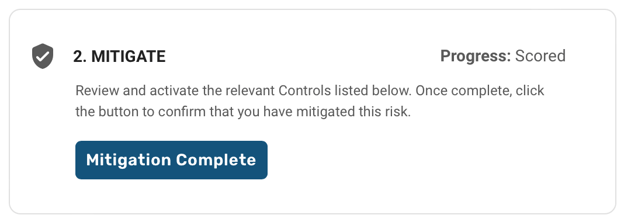
Mitigate identified risks by linking controls from one or more frameworks. You’ll be able to review and activate the relevant controls, then click a button to confirm that you have mitigated the risk.
Update risks
Continuously update risks as your company grows and changes to make sure you're always secure and audit-ready.
Strike Graph will make sure you pass your next audit with flying colors
At Strike Graph, we take the complain out of compliance. We strive to continue to offer our customers only the best, most innovative, and streamlined solutions. This way, compliance can go from a task no one is looking forward to doing to something everyone can tackle collaboratively and painlessly.
Want to see how our new features like the risk assessment, low-code integrations, multi-framework mapping, Strike Graph Teams, and more work in real time? Open your free account today and give them a spin!
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)