Everything you need to know about security compliance
Whether you're new to cybersecurity or expanding an already robust security stance, we have resources to support your learning.
Recommended:
.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(20).png)
February 12, 2026
How to Conduct CMMC Level 2 Self-Assessment: Step-by-Step with Templates
.png?width=1200&height=700&name=Blog%20Featured%20Image%20600x350px%20(19).png)
January 28, 2026
Security is not one-size-fits-all. It never has been.

December 30, 2025
How to Create an Effective CMMC SSP: Steps, Key Sections, & Starter Kit

December 18, 2025
Can AI perform a security audit? It’s already starting to

December 17, 2025
Five Predictions on CMMC’s Impact to the Defense Industrial Base in 2026
.png?width=1200&height=700&name=Blog%20Featured%20Image%20600x350px%20(12).png)
December 17, 2025
Why AI-Native Compliance Platforms Outperform AI-Enhanced Solutions
.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(17).png)
December 11, 2025
CMMC Level 1 Self-Assessment: Steps, Submission, Free Tools, and Video

December 10, 2025
How AI Is Transforming CMMC Delivery—and Accelerating Readiness
.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(13).png)
October 23, 2025
CMMC vs. ISO 27001: Similarities, Differences, Mapping, and Bundling

October 03, 2025
CMMC vs. FedRAMP: Understanding Differences and Which You Need
%20(1).png?width=1920&height=1080&name=Video%20Thumbnail%20(1)%20(1).png)
August 27, 2025
AI in GRC: How AI Is Transforming Governance, Risk & Compliance

.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(9).png)
.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(6).png)
April 16, 2025
CMMC 2.0 Level 3 Simplified: Steps, Controls and Checklist

March 24, 2025
Why SBOMs are critical for security and compliance in 2025
March 07, 2025
5 reasons not to wait to get compliant with CMMC

January 30, 2024
New Strike Graph framework | CIS builds trust without an audit
Result for
No result was found.
Guide
TrustOps implementation: an in-depth guide
Ready to take a deep dive into TrustOps? This guide gets into the nitty gritty details of how to design, operate, and measure a robust TrustOps program.
January 17, 2025
Guide
The essential TrustOps guide for 2024
If you’re waiting for the right time to tackle TrustOps, this is it. With a little planning now you can be miles ahead of the competition in the coming year, closing bigger deals faster, attracting more customers, and building brand loyalty.
December 12, 2023
Guide
Which security frameworks does my company need?
With so many compliance rules out there, it can feel like framework alphabet soup. In this guide, we go industry by industry so you know exactly what you need.
October 02, 2023
Guide
Will automation boost or break your security program?
AI and automation are great! But using them unwisely can undercut your security program. In this guide, we explore how to take a smart and effective approach.
October 02, 2023
Guide
What is governance, risk, and compliance?
Learn about GRC – governance, risk, and compliance – and how this business-wide strategy compares with TrustOps.
May 25, 2023
Guide
What cannot be shared under HIPAA?
HIPAA doesn’t need to be complicated. Explore our quick overview of what cannot be shared under HIPAA and take the first step toward compliance.
November 03, 2022
Guide
Looking for a SOC 2 report example? Here you go!
This SOC 2 report example contains commonly reviewed SOC 2 security controls and keys systems, so you can better understand what to expect.
September 30, 2022
Guide
Is your EdTech security robust enough?
Learn about the security risks EdTech companies face, and how your company can build resilience against threats through cybersecurity compliance.
September 16, 2022
Guide
CCPA vs. GDPR
Don’t know if your organization needs to be CCPA or GDPR compliant? Start here.
September 02, 2022
Guide
What is the ISO 27000 series?
Learn everything you need to know about improving your organization’s information security with the ISO 27000 series standards
August 25, 2022
Guide
5 things startups need to know about HIPAA compliance
New to the health tech space and unsure about HIPAA? Strike Graph's guide helps clarify the confusion and put you on the right track to compliance.
July 25, 2022
Guide
Guides 5 things a founder should know about SOC 2
Unsure where to start on your SOC 2 compliance journey? We're here to help guide you each step of the way.
July 21, 2022
Case Study
Clockwork achieves SOC 2 Type I in just eight business days with Strike Graph
Clockwork achieved SOC 2 Type I in just 8 business days using Strike Graph’s AI-driven compliance platform, cutting prep time by up to 50%.
November 17, 2025
Case Study
Black Mountain Software cuts security questionnaire time by 77% with AI Security Assistant
See how Black Mountain Software saves hours on vendor questionnaires and SOC 2 prep with Strike Graph’s AI-native compliance platform.
October 20, 2025
Case Study
Cleo cuts compliance time by 80% with Strike Graph
Cleo slashed compliance prep time by 80% using Strike Graph, achieving SOC 2 certification and accelerating business growth with enhanced security and development practices.
July 17, 2025
Case Study
How Bennett/Porter achieved SOC 2 compliance with minimal resources and maximum ROI
Discover how Bennett/Porter achieved SOC 2 compliance in under a year with minimal resources and maximum ROI using Strike Graph's platform.
May 22, 2025
Case Study
Martus Solutions: What previously took 3 hours now takes 15 minutes.
Strike Graph helped Martus cut security questionnaire time from 3 hours to 20 minutes and streamline SOC 2 compliance with automation and ease.
May 05, 2025
Case Study
HuLoop boosts compliance for highly regulated customers with Strike Graph
HuLoop Automation achieved SOC 2 Type 2 and built trust with financial clients by streamlining compliance with Strike Graph’s audit-ready platform.
April 28, 2025
Case Study
How Strike Graph helped LeadScorz strengthen security & breeze through SOC 2
Strike Graph helped LeadScorz pass two SOC 2 audits, reduce compliance effort, and build a trustworthy platform for sensitive customer data.
April 25, 2025
Case Study
How PayLynxs achieved compliance 50% faster– and removed sales barriers with Strike Graph
Discover how PayLynxs achieved SOC 2 compliance in half the time with Strike Graph’s AI-powered GRC platform—streamlining audits, reducing sales friction, and enabling continuous compliance.
March 25, 2025
Case Study
Ascellus: Scaling compliance through Strike Graph without scaling complexity
Discover how Ascellus streamlined compliance processes and scaled efficiently using Strike Graph’s innovative platform, enhancing stakeholder engagement and maximizing limited resources.
February 14, 2025
Case Study
ORM Technologies: SOC 2 30% faster
Learn how ORM Technologies achieved SOC 2 30% faster with Strike Graph.
February 14, 2024
Case Study
Visible: Shifting SOC 2 from resource obstacle to marketing asset
Discover how Visible reduced its sales cycle time by 30% using Strike Graph’s compliance and certification platform.
October 18, 2023
Case Study
DocuPhase: 50% less work with multi-framework mapping
Learn how DocuPhase shifted from a reactive to proactive security approach and cut their HIPAA work in half with Strike Graph.
October 16, 2023
Case Study
Catalyst Solutions: From bogged down to boosting sales
Learn how Catalyst Solutions used the Strike Graph compliance and certification platform to overcome significant compliance gaps and reach SOC 2 compliance with fast.
September 27, 2023
Case Study
Achieving compliance with HIPAA and SOC 2
Learn how GoReact — an award-winning, cloud-based video platform — obtained SOC 2 and HIPAA compliance in a matter of just weeks thanks to Strike Graph.
April 14, 2023
Case Study
How BioAgilytix got ISO 27001 certified 2x faster
How BioAgilytix Got ISO 27001 Certified 2x Faster. BioAgilytix, a seasoned team of highly experienced scientific and QA professionals, knew that despite their success in delivering best-in-class science, ISO 27001 was outside their scope of expertise. So they came to Strike Graph for help.
August 17, 2022
Case Study
How Strike Graph helped BugSplat move closer to SOC 2 compliance
How Strike Graph Helped BugSplat Move Closer to SOC 2 Compliance
July 28, 2022
Case Study
Satisfying customers and landing more contracts: NROC’s SOC 2 journey
Learn how NROC completed a Type 1 and a Type 2 audit within one year, positioning themselves for more revenue opportunities.
July 28, 2022
Case Study
Foundation AI: gaining trust and winning deals through SOC 2
Learn how Foundation AI benefited from Strike Graph’s security packet and collected evidence for SOC 2 with minimal effort.
July 28, 2022
Case Study
LCvista saved time, money, and resources with Strike Graph
LCvista Saved Time, Money, and Resources With Strike Graph
July 28, 2022
Blog
How to Conduct CMMC Level 2 Self-Assessment: Step-by-Step with Templates
Experts explain each step in a CMMC Level 2 self-assessment. Get the free self-assessment tool, plus templates for gap analysis, SSP, and POA&M.
February 12, 2026
Blog
Security is not one-size-fits-all. It never has been.
Uncover the pitfalls of standardized security compliance and the urgent need for genuine auditor independence and transparency in the wake of the recent SaaS Audit Leak.
January 28, 2026
Blog
How to Create an Effective CMMC POA&M: Steps, Best Practices and Starter Kit
Experts share tips to simplify POA&Ms. Learn best practices and accelerate your path to CMMC compliance. Free CMMC POA&M Starter Kit & template.
January 14, 2026
Blog
How to Create an Effective CMMC SSP: Steps, Key Sections, & Starter Kit
Compliance experts break down the CMMC SSP process into manageable steps. Also, get a free SSP starter kit with a guided template, SSP examples, and tip sheets.
December 30, 2025
Blog
Can AI perform a security audit? It’s already starting to
Discover how AI is transforming security audits from costly, inefficient processes to dynamic, continuous assurance, enhancing both speed and accuracy in compliance management.
December 18, 2025
Blog
Five Predictions on CMMC’s Impact to the Defense Industrial Base in 2026
Strike Graph's CEO Justin Beals shares five predictions on how CMMC implementation will reshape the defense industrial base by 2026.
December 17, 2025
Blog
Why AI-Native Compliance Platforms Outperform AI-Enhanced Solutions
Discover why AI-native compliance platforms deliver higher accuracy, continuous validation, stronger security, and lower costs than AI-enhanced solutions.
December 17, 2025
Blog
CMMC Level 1 Self-Assessment: Steps, Submission, Free Tools, and Video
Experts explain each step in a CMMC Level 1 self-assessment. This guide includes how-to videos, a gap analysis template, and a free CMMC self-assessment tool.
December 11, 2025
Blog
How AI Is Transforming CMMC Delivery—and Accelerating Readiness
Discover how AI is revolutionizing CMMC delivery by automating evidence collection, speeding up gap identification, enabling continuous readiness, and accelerating documentation creation.
December 10, 2025
Blog
CMMC vs. NIST 800-171: Comparing, Mapping and Streamlining Compliance
See how NIST 800-171 & CMMC overlap and differ. Learn about the time and cost of compliance & how to implement and streamline it. Free CMMC vs NIST 800-171 control mapping.
October 24, 2025
Blog
CMMC vs. ISO 27001: Similarities, Differences, Mapping, and Bundling
Compliance experts simplify how these two certifications overlap and explain how to integrate and implement them efficiently. Full control & evidence mapping download.
October 23, 2025
Blog
Why compliance leaders struggle with confidence — and how AI can change that
With only 4.4% of leaders fully confident in their compliance programs, AI is reshaping how organizations build trust by delivering continuous visibility.
October 07, 2025
Blog
CMMC vs. FedRAMP: Understanding Differences and Which You Need
Learn the key differences between CMMC and FedRAMP. Learn who needs which framework, and download a free control mapping spreadsheet.
October 03, 2025
Blog
AI-native vs. AI-powered: Why architecture matters in the age of intelligence
AI-native vs. AI-powered: discover why AI-native architecture matters for compliance. Learn how AI-native delivers security, accuracy, and agentic automation.
October 02, 2025
Blog
AI in GRC: How AI Is Transforming Governance, Risk & Compliance
GRC & AI experts explain how AI is transforming GRC today and what’s next. Learn about tools, benefits, challenges, and see real-world examples. Includes video.
August 27, 2025
Blog
Medical Device SBOMs Simplified: Role, FDA Requirements, Examples & Checklist
Experts break down the FDA’s medical device SBOM mandate. Learn why SBOMs matter & get implementation advice. Download a free FDA SBOM compliance checklist.
August 27, 2025
Blog
Automated to AI-Powered Evidence Collection in Compliance: Benefits, Challenges, & Trends
Learn how automation & AI evidence collection help you avoid audit surprises. Explore real-world use cases, key benefits & implementation tips. Multiple videos.
August 13, 2025
Blog
AI-Powered Compliance Monitoring: Capabilities, Benefits, Examples, and Trends
Learn how AI compliance monitoring helps companies reduce risk, improve accuracy, and stay audit-ready. See examples, benefits, and where the tech is heading.
August 13, 2025
Blog
Medical device & healthcare SBOMs: Best practices by type and format
Experts share and discuss best practices for medical devices and healthcare systems SBOMs by type and format. Download best practices cheat sheet & watch a video.
July 30, 2025
Blog
Gen AI, Agentic AI & AGI for Internal Compliance Audits: The Future Has Already Started
Discover how compliance teams use AI to improve audit speed, accuracy & insight. Learn how Gen AI & Agentic AI are reshaping internal audits & what to do next.
June 20, 2025
Blog
CMMC 2.0 Level 3 Simplified: Steps, Controls and Checklist
Experts break down CMMC 2.0 Level 3 for defense contractors with tips to streamline compliance. Download a free list of controls and a task checklist.
April 16, 2025
Blog
Why zero trust architecture is reshaping security and compliance programs
Explore how Zero Trust and AI-powered automation are redefining security and compliance—and how Strike Graph helps teams stay secure and audit-ready.
April 03, 2025
Blog
Why SBOMs are critical for security and compliance in 2025
Discover why Software Bill of Materials (SBOMs) are essential for security and compliance in modern software development and how automated solutions can streamline SBOM management.
March 24, 2025
Blog
Simplifying CMMC audits: step-by-step preparation, best practices and checklist
Compliance experts break down CMMC audit types and share step-by-step prep. See cost and time estimates. Download a free CMMC Audit Task Checklist.
March 13, 2025
Blog
Simplifying TISAX Audits: Types, Steps, Streamlining Strategies and Checklist
Experts explain the types and objectives of TISAX audits. Tips on preparing for the audit, passing & earning a TISAX label. Download Free Audit Checklist.
March 11, 2025
Blog
5 reasons not to wait to get compliant with CMMC
Discover why immediate action on CMMC compliance is crucial for defense contractors and how modern solutions can streamline the process. Stay competitive and secure your DoD contracts now.
March 07, 2025
Blog
How Strike Graph’s unique software architecture has helped shape five years of success
Discover how Strike Graph's unique AI-driven software architecture revolutionizes compliance, offering unmatched flexibility and scalability for organizations tackling multiple security frameworks.
February 20, 2025
Blog
Customer-centric design: The driving force behind Strike Graph’s innovation
Discover how Strike Graph's customer-centric design approach drives innovation in security and compliance solutions, ensuring user needs shape product development and enhance customer success.
February 14, 2025
Blog
CMMC 2.0 Level 2 Simplified: Requirements, Steps, Controls List and Checklist
Experts explain the new CMMC 2.0 Level 2 framework for defense contractors step by step. Download a free Level 2 security control list & CMMC Level 2 checklist.
February 07, 2025
Blog
Strike Graph Ranks #1 for Results and Implementation on G2
Strike Graph ranks #1 for Results and Implementation in G2 Winter 2025 Reports, showcasing its excellence in compliance management and customer trust.
January 22, 2025
Blog
Top 3 predictions for 2025 and the future of enterprise compliance
Simplify compliance with centralized, automated, and scalable solutions. Learn how Strike Graph's innovative tools can streamline your compliance efforts and reduce errors in 2025 and beyond.
January 15, 2025
Blog
Announcing the launch of enterprise content management at Strike Graph
Discover how Strike Graph's new enterprise content management feature streamlines compliance, reduces redundancies, and automates control mappings for organizations with multiple locations or subsidiaries.
December 20, 2024
Blog
PCI attestation of compliance (AOC): components, steps, samples, and starter kit
Learn to complete a PCI AOC from experts. Avoid common AOC errors to become PCI compliant. Download a free PCI DSS Starter Kit with AOC samples and templates.
November 27, 2024
Blog
Breaking Down the Penetration Testing Process: Phases, Steps, Timelines, and Industry-Specific Strategies
Pen test experts explain each phase, main steps and timing. Learn how AI can streamline the pen testing process. Download free Pen Testing Schedule Template.
November 13, 2024
Blog
Mastering PCI DSS scoping: categories, steps, and how to reduce scope
Compliance experts explain PCI scoping categories, walk you through the process step-by-step, help you reduce your scope & provide a Free PCI Scope Toolkit.
October 29, 2024
Blog
October Product Roundup
Explore Strike Graph's new Quick Start feature, designed to automate evidence collection and streamline compliance with AI-powered tools, ensuring you're always audit-ready.
October 28, 2024
Blog
Strike Graph’s strategic approach to AI in compliance
Discover how Strike Graph's AI-driven tools enhance security compliance with automated data collection, intelligent control testing, and real-time evidence validation.
October 28, 2024
Blog
What You Need to Know About CMMC in 2025
Learn the ins and outs of CMMC 2.0 compliance and how it impacts your business.
October 24, 2024
Blog
Strike Graph now offers hosted data within the EU
Strike Graph now offers data hosting in the European Union for customers with specific data privacy and security requirements.
October 08, 2024
Blog
Penetration testing best practices: ensuring consistent and effective security testing
Compliance experts share best practices for pen testing. Learn how to choose the best pen test vendor for your use case. List of Pen Testing Vendor Questions.
September 26, 2024
Blog
PCI DSS v4.0 (v4.0.1): Requirements, changes, implementation steps and checklist
PCI DSS compliance experts share the new requirements and changes in PCI DSS v4.0.1. Also, get a v4.0 implementation roadmap and a free PCI DSS v4.0 checklist.
September 10, 2024
Blog
PCI DSS policy essentials: requirements, examples & templates
PCI experts share everything you need to include in a PCI policy for v4.0.1. Free PCI policy template, tips for customizing & how to make compliance easier.
August 27, 2024
Blog
Beyond SBOMs: Building a secure future for medical devices
The FDA's SBOM mandate is a positive step, but companies should need to implement a comprehensive cybersecurity framework to fully protect devices, users, and ultimately, patient safety.
August 26, 2024
Blog
Enhancing Infrastructure Security: A Shift Towards HTTP/S Retrieval Systems
Explore the hidden security risks of software agents and discover how network segmentation and HTTP/S retrieval systems can enhance your IT infrastructure.
August 19, 2024
Blog
Lessons from the CrowdStrike outage: Why verification is the missing piece in modern security automation
Wondering which security frameworks might be helpful for your organization? Read on to learn about some of most common standards and certifications.
July 24, 2024
Blog
Navigating GDPR: How to protect data subject rights
Find out how to navigate GDPR and protect your data subject rights with Strike Graph's easy-to-follow guide. It's all about staying compliant and building trust, the smart way!
April 18, 2024
Blog
Navigating the Evolving Security Landscape: An In-Depth Look at the Gartner Security & Risk Management Summit
Learn how a well-planned cybersecurity certification roadmap can streamline your compliance process, saving time and reducing stress.
April 12, 2024
Blog
Streamlining security compliance: the essential cybersecurity certification roadmap
Learn how a well-planned cybersecurity certification roadmap can streamline your compliance process, saving time and reducing stress.
April 11, 2024
Blog
Empowering innovation through customized compliance: the Strike Graph advantage
Discover how Strike Graph's comprehensive platform transforms compliance for tech-forward companies with customizable controls, collaboration tools, and strategic insights for unparalleled agility and security.
April 04, 2024
Blog
Simplifying compliance together: Here's what our customers are saying about Strike Graph
Discover what our customers are saying about their journey to simplified compliance with Strike Graph! From stress-free certifications to the power of AI and automation, learn how we turn the compliance process into a streamlined, revenue-boosting experience.
April 01, 2024
Blog
Simplifying data security compliance in a complex regulatory landscape
Don’t let compliance with multiple security frameworks bog you down. Strike Graph’s multi-framework data security compliance platform streamlines the process.
March 28, 2024
Blog
Penetration tests vs. vulnerability scans
Learn how pen testing and vulnerability scanning combat AI cyber threats to fortify your data security in our essential guide.
March 26, 2024
Blog
Decoding the HIPAA Omnibus Rule: A guide for HealthTech professionals
Navigate the complexities of the HIPAA Omnibus Rule with insights on achieving and proving compliance, crucial for HealthTech professionals looking to safeguard patient information.
March 25, 2024
Blog
The key to understanding SOC reports
Everything you need to know about SOC 1, SOC 2, and SOC 3 reports, including what’s in them and the benefits they can offer your business.
March 14, 2024
Blog
Strike Graph now supports the HIPAA privacy rule for covered entities!
For covered entities, meeting the standards of the HIPAA privacy rule is non-negotiable. Strike Graph empowers health-sector companies to efficiently meet these requirements and leverage their security measures to build customer trust and outperform the competition.
February 26, 2024
Blog
Strike Graph solves the unique HIPAA challenges of HealthTech
HealthTech companies face unique challenges when it comes to security and privacy — including HIPAA compliance. Here’s how Strike Graph solves them.
February 12, 2024
Blog
Risk ownership and scoring: Why Strike Graph is your go-to platform for risk-based compliance
Risk-based security compliance is a breeze with Strike Graph’s suite of risk-management tools like risk ownership and scoring.
February 09, 2024
Blog
The essential HIPAA compliance checklist for HealthTech companies
Unsure whether your HealthTech company needs to be HIPAA compliant? Here’s how HIPAA applies to HealthTech and a compliance checklist to get you started.
January 31, 2024
Blog
New Strike Graph framework | CIS builds trust without an audit
Strike Graph now supports CIS, a versatile, robust security framework for companies looking to prove their commitment to data security without committing the time and resources necessary to complete a formal audit.
January 30, 2024
Blog
Should I get GDPR and ISO 27701 at the same time? Yes!
Independently, GDPR and ISO 27701 can feel like heavy lifts — tackling GDPR and ISO 27701 together saves you both time and resources.
January 29, 2024
Blog
Closing deals the easy way: see what a difference Strike Graph makes
Independently, GDPR and ISO 27701 can feel like heavy lifts — tackling GDPR and ISO 27701 together saves you both time and resources.
January 28, 2024
Blog
4 trends shaping HealthTech compliance in 2024
4 healthcare and healthtech compliance trends to watch. and how to protect your organization. Solutions from Strike Graph, a leader in healthcare compliance.
January 25, 2024
Blog
Strike Graph and Judy Security partner to bring the best of security compliance and cybersecurity tech
Innovation benefits from thoughtful collaboration — which is why Strike Graph is pleased to announce we’ll be partnering with Judy Security to bring together the best cybersecurity and security compliance tech.
January 16, 2024
Blog
Enhancing collaboration and efficiency: the power of control notes and comments
Bring real-time collaboration tools to your risk mitigation process with Strike Graph’s control comments and notes.
January 05, 2024
Blog
Satisfy security demands now with Strike Graph’s security overview
You need to get certified — fast. Strike Graph’s security overview gives you immediate proof that you’re in the process of securing your data.
January 04, 2024
Blog
$8.5 million in new funding propels Strike Graph’s mission to revolutionize security compliance
Strike Graph announces $8.5 million in new funding, led by BAMCAP with participation from existing investors Madrona and Information Venture Partners, and Rise of the Rest.
December 20, 2023
Blog
Comparing NIST 800-171 and 800-53: Differences, Mapping, Bundling & Streamlining
See how NIST 800-171 and 800-53 overlap and differ. Get expert tips on implementation and see the benefits of combining efforts. Free NIST 800 control mapping.
December 17, 2023
Blog
Enhance your security program with these top 5 AI best practices
Want to use AI tools, but not sure how to use them in your security program? In this post, we show you how to strategically implement 5 AI best practices.
December 14, 2023
Blog
Take your security program from resource drain to revenue builder
Traditional security approaches are inflexible, inefficient, and costly. You need a modern approach that leverages the newest technology to save you time and resources.
December 14, 2023
Blog
7 Strike Graph features that turn anyone into a security compliance expert
Ready to tackle your compliance objectives with the team you have? Here’s how the Strike Graph platform can help — no compliance expertise required.
December 13, 2023
Blog
8 steps for conducting a NIST 800-171 self-assessment
Here’s how to conduct an 8-step NIST 800-171 self-assessment and the boost it can bring to your business.
December 13, 2023
Blog
Strike Graph’s control library makes mitigating risk a breeze
Learn how using the Strike Graph control library makes it easy to put controls in place across multiple frameworks.
December 04, 2023
Blog
Save time and resources with Strike Graph’s integrated risk assessment
Tired of wasting time on checklist approaches to security compliance? Strike Graph’s in-platform risk assessment ensures you’re covering all your vulnerabilities without wasting time and money.
November 30, 2023
Video
PCI DSS vs. SOC 2: Differences, Overlaps and Streamlining Certifications
Experts explain the differences & similarities. Download free mapping of controls & evidence. Learn when to get both certifications. See time & cost savings.
November 28, 2023
Blog
PCI DSS levels 101: requirements, examples & starter kit
Our compliance experts explain the PCI DSS levels and requirements. Explore the recent changes to PCI DSS and get a free PCI DSS compliance starter kit.
November 28, 2023
Video
Video | Who must comply with PCI DSS?
Wondering if your company is subject to PCI DSS? Read on to learn who must meet PCI DSS requirements and what it takes to reach compliance.
November 27, 2023
Video
Video | SOC 2 vs. ISO 27001: Security standards for EdTech companies
Learn why SOC 2 and ISO 27001 are essential cybersecurity tools for EdTech companies.
November 21, 2023
Blog
7 reasons AI-powered compliance is crucial to your business growth
AI-powered compliance means lower costs, more accuracy, less vulnerability, and faster certification. Here’s how tech-enabled audits make this a reality.
October 23, 2023
Blog
12 SOC 2 controls that support CPRA compliance
Reduce redundancy while ensuring comprehensive coverage — among other perks. Learn how you can best leverage the framework overlap between SOC 2 and CPRA.
October 20, 2023
Blog
What to expect during your ISO 27001 and/or ISO 27701 audit
The ISO 27001 and ISO 27701 certification processes may seem complex, but armed with these tips, you’ll be able to tackle them with confidence.
October 19, 2023
Video
Video | FERPA for EdTech companies
Learn what education’s most important privacy law — FERPA — means for EdTech companies.
October 19, 2023
Blog
Prep for FedRAMP compliance using NIST 800-53
Building towards FedRAMP compliance? Become NIST 800-53 compliant first and you’ll be well on your way.
October 18, 2023
Blog
Everything you need to know about SOC 1
The ins and outs of SOC 1: What it is, why it’s important, who it’s for, the types of reports (including SOC 1 Type 1, SOC 1 Type 2, and SOC 1 Type 3) and more.
October 16, 2023
Blog
Save time and mental energy with automated evidence collection
Automated evidence collection takes the hassle out of a previously manual and tedious process, allowing you to streamline your entire compliance journey.
October 04, 2023
Blog
How multi-framework mapping can benefit your business
Here’s how the ability to map one control to multiple security frameworks can take your business to the next level.
September 20, 2023
Blog
What is SOC 3? And why your business (might) need it
Learn about what SOC 3 is, who needs it, why it’s important, and what the difference is between SOC 1, SOC 2, and SOC 3.
August 30, 2023
Blog
Introducing Strike Graph’s new AI security assistant
Save time and build a culture of trust with our new AI security assistant. Your security compliance team will thank you.
August 25, 2023
Blog
Why measuring your TrustOps or security program is essential
In the third and final installment of our series on TrustOps and security programs, we take a deep dive into how to best measure your program.
August 24, 2023
Blog
The ins and outs of operating a TrustOps or security program
In the second installment of our series, we dive into how best to operate a TrustOps or security program.
August 15, 2023
Blog
Introducing Strike Graph teams
Strike Graph’s new teams feature streamlines collaboration so you can reach compliance faster and more easily.
July 27, 2023
Blog
How to design your security program
When designing your security program, steer clear of expensive consultants and certification-in-a-box approaches — opt for a holistic approach instead.
July 14, 2023
Blog
Strike Graph’s trust asset library turns compliance into revenue
Strike Graph’s Trust Asset Library can help keep all of your trust assets in one central location, making it easier to store, locate, and share them.
July 13, 2023
Blog
Has the Data Protection Act of 1988 been repealed?
Learn about the status of the Data Protection Act of 1988 and the updates it has undergone in recent years.
July 04, 2023
Blog
Is the Data Protection Act of 1988 still in force?
Learn about the Data Protection Act of 1988, how it has changed over time, and where it intersects with GDPR.
June 30, 2023
Blog
How many controls are there in ISO 27001:2022?
With ISO 27001:2022, there are 93 instead of 114 controls, including 11 new ones. In this post we take a closer look at what those are.
June 30, 2023
Blog
What is FedRAMP and how can you get FedRAMP authorized?
FedRAMP is an important standardized approach that agencies can use to assess the use of federal data — read on to learn what that means and why it matters
June 28, 2023
Blog
How mature is your security program?
Ready to improve your security program, meet compliance requirements, improve stakeholder trust, and increase revenue? Moving up in the TrustOps maturity model makes it happen.
June 20, 2023
Blog
The Strike Graph HIPAA certification is here!
A new HIPAA certification is here. Learn what you need to do in order to achieve certification and how Strike Graph can help.
June 20, 2023
Blog
Collision 2023 – compliance tech to build trust
The leading provider of automated security compliance solutions, Strike Graph, will be at Collision Conference in Toronto June 26-29, 2023.
June 15, 2023
Blog
TISAX requirements
What are the TISAX requirements? What are the labels, and how are they different? Let’s take a deep dive.
June 06, 2023
Blog
TISAX Levels Simplified: Differences, Preparations & Checklists
TISAX experts compare the 3 assessment levels and detail how to reach compliance for each. Explore time and costs. Download Free TISAX Preparation Checklist.
May 26, 2023
Blog
Combine software and service to optimize your security program
Pairing Strike Graph’s all-in-one compliance platform with a service provider like GoldSky can deliver a turn-key security program.
May 26, 2023
Blog
Strike Graph now supports TISAX for automotive success
Strike Graph is excited to announce that we now support TISAX — the emerging global standard for companies in the automotive industry.
May 18, 2023
Blog
TISAX vs. ISO 27001: Similarities, Differences, Mappings & Streamlining
Compliance experts explain TISAX vs ISO 27001. Learn similarities & differences and when to get one or both certifications. Free mapping of controls & evidence.
May 17, 2023
Blog
How to become HIPAA compliant — and why you should
Becoming HIPAA compliant can help spare your business from costly violations. Learn more about HIPAA, who is regulated, and how to get compliant.
April 25, 2023
Blog
How do I transition from ISO 27001: 2013 to ISO 27001: 2022?
Learn when you need to transition from ISO 27001: 2013 to ISO 27001: 2022, what’s changing, and what’s staying the same.
April 24, 2023
Blog
What are trust assets, and how do they grow your revenue?
Trust assets, like certifications, prove your company is trustworthy, which boosts revenue — and they don’t have to be difficult to achieve.
April 21, 2023
Blog
What is a chief trust officer (CTrO)
Learn what a Chief Trust Officer (CTrO) does, why they’re important, and how robust reporting can make their lives easier.
April 14, 2023
Blog
What is TrustOps and why does it matter for your business?
TrustOps is all about building trust with customers and partners. Learn why TrustOps is important for your business and how to get started.
April 13, 2023
Blog
Don’t get caught off guard by the next banking crisis
In light of the SVB crisis, you may be asking what your company should do next. We have the answer — it’s time to mitigate banking risk. Here’s how.
March 31, 2023
Blog
Who needs CMMC certification?
Understanding all the ins and outs of CMMC can be difficult, but we’re here to help. Here’s who needs CMMC certification and how to achieve it.
March 21, 2023
Blog
How do I conduct a vendor risk assessment?
Learn the six stages of conducting a vendor risk assessment and know what types of risk you should be checking for with potential partners.
March 21, 2023
Blog
What are the 6 stages of risk management?
Ready to ensure a strong security posture? Start with risk management. In this post we explain the 6 stages of risk management and how you can prepare for each.
March 18, 2023
Blog
Everything you need to know about the SOC 2 audit process
Need to get SOC 2 compliant ASAP? This guide will walk you through everything you need to know about the SOC 2 audit process so you can go in prepared.
March 14, 2023
Blog
How do I become SOC 2 Type 2 compliant?
Does your organization need to become SOC 2 Type 2 compliant? Here’s how to know, and how to get there if you do.
February 23, 2023
Blog
The difference between SOC 1 and SOC 2
What’s the difference between a SOC 1 and SOC 2? What about a SOC 1 Type 1 and Type 2 and a SOC 2 Type 1 and Type 2? In this post, we break it all down.
February 21, 2023
Blog
What was the data protection act of 1988?
Learn about the history of the data protection act of 1988 and its evolution into the GDPR.
February 16, 2023
Blog
How Strike Graph's AI-powered platform transforms compliance and accelerates security certifications
Strike Graph now includes security certifications. Our all-in-one platform takes you from start to certification — no auditing firm required.
February 15, 2023
Blog
Who must comply with SOC 2 requirements
Learn about who needs to comply with SOC 2 requirements, and all the benefits of achieving compliance.
February 13, 2023
Blog
Announcing a smarter way to get security certifications
Strike Graph announces a new integrated solution that allows customers to go through security audits powered by technology at a fraction of the cost and time.
February 08, 2023
Blog
Can you fail a SOC 2 audit?
Learn why SOC 2 audits aren’t pass-fail, the importance of an auditor opinion, and how to prepare for an audit.
February 02, 2023
Blog
How much does a SOC 2 audit cost?
A SOC 2 audit costs a lot less when you use an all-in-one solution instead of a traditional auditing firm. Here’s why.
February 01, 2023
Blog
6 types of vulnerability scanning
Are you performing vulnerability scanning? Here’s why you should and what types of scans are available to ensure your business is secure.
January 27, 2023
Blog
What is a network security test?
Learn about network security tests, their benefits, and how Strike Graph can help you with testing.
January 26, 2023
Blog
Why are governance, risk, and compliance important?
Explore why governance, risk, and compliance (GRC) are important for your organization and learn how you can get started.
January 26, 2023
Blog
Compliance attestation: What it is and how it affects your business
Do you know the difference between certification and attestation? In this post we explore what compliance attestation is and how it affects your business.
January 25, 2023
Blog
Regulatory compliance software: Which should you choose?
Regulatory compliance software provides organizations with a framework to stay up to date with regulatory requirements and avoid compliance breaches.
January 22, 2023
Blog
The CPRA – California Privacy Rights Act – is here!
The CPRA went into full effect on January 1, 2023 — is your business ready?
January 13, 2023
Blog
What is a security audit and how can it benefit your small business?
Security audits may seem overwhelming at first, but don't worry — in this guide, we'll break down what they are and how they benefit your business.
January 09, 2023
Blog
What is compliance tracking?
Compliance tracking is the process of monitoring and organizing compliance-related information and activities. Here’s how your business can do it.
December 29, 2022
Blog
Do you need an ISO 27001 audit in 2023? Probably!
Learn why ISO 27001 audits are important for businesses managing sensitive information.
December 27, 2022
Blog
Security compliance for startups: 3 reasons you need to start now
Lack of security compliance could cost your startup millions and ruin your reputation. Learn why you should implement a security plan now for future success.
December 22, 2022
Blog
What is the purpose of compliance risk management?
If your company doesn’t have a compliance risk management plan, you could be facing a loss of reputation, revenue, valuation, and business opportunities.
December 20, 2022
Blog
Strike Graph now offers NIST 800-171
Our NIST 800-171 compliance support can help your organization better protect CUI and even achieve CMMC certification.
December 14, 2022
Blog
What is cybersecurity governance?
Discover how your leadership team can use a cybersecurity governance plan to fortify your organization against increasing cybersecurity threats.
December 12, 2022
Blog
HITRUST vs. HIPAA
Explore the relationship between the Health Insurance Portability and Accountability Act of 1996 and the security framework that proves you’re in compliance with it.
November 25, 2022
Blog
What are the NIST SP 800-171 controls?
Get all the details on the NIST SP 800-171 controls and how they apply to your organization.
November 23, 2022
Blog
What is an information security policy, and do you need one?
Creating a strong information security policy can help your organization prevent data breaches, and more. Discover what your policy should include.
November 22, 2022
Blog
What is NIST certification?
Here’s what your business will need to do in order to obtain NIST certification — actually NIST compliance — including NIST SP 800-171.
November 17, 2022
Blog
What are the 5 steps in the NIST cybersecurity framework?
Implementing the 5 steps in the NIST cybersecurity framework will help your business stay protected against potential security threats.
November 16, 2022
Blog
A cheatsheet for common GDPR terms
There are a lot of GDPR terms, and it can be difficult to keep them all straight. Hopefully this cheatsheet will help you on your journey to GDPR compliance.
November 16, 2022
Blog
SOC 2 Type 1 vs Type 2 — What’s the difference?
SOC 2 is quickly becoming one of the most important compliance frameworks for businesses. Which one should your business pursue – SOC 2 Type 1 or Type 2?
November 02, 2022
Blog
What are the 7 types of risk to your business?
While no company is risk-free, you can mitigate many kinds of risk with proper understanding and an action plan. Learn how!
October 31, 2022
Blog
What is required for GDPR compliance?
What exactly is required of your organization in order to achieve — and maintain — GDPR compliance? Let’s take a look.
October 25, 2022
Blog
Understanding cybersecurity compliance
What is compliance in cybersecurity? Why is compliance important? Read on to learn cybersecurity basics and how you can achieve compliance, quickly.
October 24, 2022
Blog
How many controls are there in ISO 27701?
Check out our overview of ISO 27701 controls for your answer, including what controls are, how they work, and how they improve your data security posture.
October 19, 2022
Blog
What is a vendor risk assessment questionnaire?
A vendor risk assessment questionnaire helps organizations identify their partners’ potential weaknesses that could result in a breach.
October 18, 2022
Blog
Unlock revenue with HIPAA compliance
Learn how HIPAA compliance can boost your company’s revenue and set you up for future success.
October 11, 2022
Blog
What are the rule exceptions to HIPAA?
HIPAA rule exceptions include state and federal exceptions, operational and occupational exceptions, emergency situation exceptions, and more.
October 07, 2022
Blog
Top 5 things our customers love about Strike Graph
See what our customers have to say about the Strike Graph security compliance platform on G2.
October 05, 2022
Blog
What are the 8 GDPR rights?
The GDPR establishes eight rights for individuals on the internet. Read about these rights and your organization's responsibilities to protect them.
September 28, 2022
Blog
What are the exceptions to CCPA?
Find out if your company or any of the information you handle is exempt from the CCPA.
September 26, 2022
Blog
What is a PCI Qualified Security Assessor?
If your company needs to undergo a PCI DSS audit, it will be performed by a PCI Qualified Security Assessor. Here’s how they’ll assess your compliance.
September 21, 2022
Blog
Unstructured data and its impact on SOC 2 compliance
A SOC 2 report ensures that service providers are securely managing your unstructured data to defend your organization’s security and privacy.
September 15, 2022
Blog
Succeed together — from far apart
The team at Strike Graph is fully remote. This means we succeed together via a culture of collaboration and smart remote work strategies.
September 08, 2022
Blog
Who needs to comply with the CCPA?
To ensure your business is CCPA compliant, you need to know what CCPA is, who needs to comply, and what happens if you don’t.
September 07, 2022
Blog
How much does ISO 27001 certification cost?
Learn about the cost of ISO 27001 certification and maintenance and decide whether the benefits of ISO 27001 outweigh the costs.
August 31, 2022
Blog
ISO 27001 controls
ISO 27001 certification proves you can protect sensitive information. Read on to learn more about ISO 27001 controls and how to implement them.
August 30, 2022
Blog
The HIPAA Privacy Rule: Is your organization a covered entity?
Learn who the HIPAA Privacy Rule applies to, which information it protects, and how your organization can reach compliance.
August 23, 2022
Blog
ISO vs. GDPR Compliance: Similarities, Differences, Mappings & Streamlining
Experts explain the differences & similarities between GDPR, ISO 27001:2022 and ISO 27701. Download free mapping of controls & evidence. Learn when to combine.
August 18, 2022
Blog
Security frameworks 101
Wondering which security frameworks might be helpful for your organization? Read on to learn about some of most common standards and certifications.
August 16, 2022
Blog
Who must comply with PCI DSS?
Wondering if your company is subject to PCI DSS? Read on to learn who must meet PCI DSS requirements and what it takes to reach compliance.
August 12, 2022
Blog
What are the 3 rules of HIPAA?
When it comes to the 3 rules of HIPAA — the Privacy Rule, the Security Rule, and the Breach Notification Rule — what do you need to know?
August 09, 2022
Blog
We achieved SOC 2 Type 2 compliance!
Strike Graph has reached SOC 2 Type 2 compliance! Learn what the experience taught us and how it can benefit you.
August 05, 2022
Blog
What is TPRM or third-party risk management?
TPRM stands for third-party risk management. Learn about the benefits and challenges of implementing TPRM controls for your organization.
July 26, 2022
Blog
What is summary health information?
Learn how HIPAA defines summary health information, the Privacy Rule, PHI, and more — and how they apply to your business.
July 25, 2022
Blog
SOC 1 vs. SOC 2 vs. SOC 3: Differences, Decision Tree, Checklists & AI Efficiencies
Compliance experts explain the differences, benefits, and challenges of SOC 1, SOC 2, and SOC 3. See which you need, and get our free SOC compliance checklist.
July 24, 2022
Blog
What is compliance risk?
Learn about compliance risk and the strategies and frameworks used to manage it.
July 23, 2022
Blog
Get your business ready for the California Privacy Rights Act (CPRA)
On January 1, 2023, the California Privacy Rights Act (CPRA) will take effect. Is your business ready to make the shift?
July 21, 2022
Blog
What are the 4 PCI DSS levels?
The 4 PCI standards—or PCI DSS compliance levels—are an important part of the PCI DSS certification process. Learn what defines PCI DSS Levels 1, 2, 3 & 4.
July 21, 2022
Blog
What are the 7 GDPR principles?
Let's take a look at all 7 principles of GDPR and what they mean for you and your business. Learn more.
June 24, 2022
Blog
Comparing ISO 27001 & ISO 27701: Differences, similarities, and dual certification process
Learn how these frameworks overlap and differ. See how to save time & money by doing both certifications at once. Plus, implementation tips & free checklist.
June 21, 2022
Blog
The 12 PCI DSS requirements: an in-depth look
Let's go a bit more in-depth and explore the 12 PCI DSS requirements, as well as how they apply to your business.
June 08, 2022
Blog
From cost concern to opportunity maker
Justin Beals, CEO at Strike Graph and David Penn, Research Analyst with Finovate talk about the current compliance landscape and how to find the right partner for your unique business.
June 03, 2022
Blog
Need a quick guide to GDPR? Start here.
Regardless of where you’re located, if your business collects and/or manipulates the personal data of EU residents, then you need to comply with GDPR.
May 27, 2022
Blog
Strike Graph now supports PCI DSS
Strike Graph now supports PCI DSS to help you increase cardholder data controls and secure credit and debit card transactions against fraud and data theft.
May 16, 2022
Blog
What is PCI DSS?
Is your business collecting credit card data? Make sure you know the risks and how to stay PCI DSS compliant. Strike Graph streamlines PCI DSS.
May 16, 2022
Blog
CCPA / CPRA compliance: What you need to know
The California Consumer Privacy Act (CCPA) was signed into law on June 28, 2018 and became effective on January 1, 2020. Here's what you need to know.
May 04, 2022
Blog
SOC 2 Report Example
What is a SOC 2 Attestation Report? It’s the pot of gold at the end of the service authorization control (SOC 2) audit journey. These reports—issued by ind
April 08, 2022
Blog
ISO 27701 basics
Learn more about what ISO 27701 is, why it’s important, and how Strike Graph can help your organization achieve certification.
April 07, 2022
Blog
Compliance in the education technology industry
What does compliance mean for education technology? Get the scoop on FERPA (Family Educational Rights and Privacy Act) and why compliance in education matters.
April 02, 2022
Blog
Understanding and accelerating security questionnaires
Learn how security questionnaires are used and how to speed up the sales process.
March 24, 2022
Blog
Auditors and security controls: where to draw the line
CPA auditors aren't the experts of security and governance controls. Listen as Justin Beals & Sam Oberholtzer discuss the taboos of audit culture.
March 11, 2022
Blog
The six stack: 6 software solutions for startup success
Choosing the right software for managing your business can be daunting, especially for the startup. With a bit of guidance, it does not have to be.
March 10, 2022
Blog
Strike Graph compliance made easy
Strike Graph helps simplify security certifications like SOC 2, ISO 27001, ISO 27701, HIPAA, CCPA, and GDPR to achieve trust and move deals.
March 08, 2022
Blog
Cybersecurity Frameworks 101
Understanding IT security frameworks and which one applies to your organization can be confusing. We've broken it down and made it simple for you.
March 05, 2022
Blog
12 vendor management best practices
Read these 12 Vendor management best practices help you increase the value from your vendor relationships.
March 02, 2022
Blog
AICPA guidance and SOC 2 audit practices
Strike Graph CEO Justin Beals discusses the intricacies of SOC 2 Audits and audit practices with experts Sam Oberholtzer and Michelle Strickler.
February 28, 2022
Blog
How our customers achieve success with flexible compliance management
Manager of Customer Success Jordan Bellman reflects on how Strike Graph's flexible platform helps her clients achieve their compliance goals.
February 22, 2022
Blog
The differences between ISO 27002: 2013 and ISO 27002: 2022
ISO 27002 provides guidance on the implementation of controls from ISO 27001 Annex A. On February 15, 2022, ISO 27002: 2013 was updated to 27002: 2022.
February 17, 2022
Blog
Penetration testing costs: Key factors, pricing insights and cost management
Compliance experts share average costs, factors affecting pricing, and pricing models. See questions to ask vendors before buying pen testing.
February 15, 2022
Blog
Strike Graph now supports ISO 27701
Strike Graph now supports ISO 27701, a standard for privacy information management that helps companies stay ahead of the compliance curve.
February 10, 2022
Blog
Understanding regulation, security, governance, and compliance
Justin Beals joins Sam Oberholtzer to discuss regulation, security, governance, and compliance. Learn what they mean and how they're connected.
February 01, 2022
Blog
Antivirus software: helpful or harmful?
Learn why employing an anti-virus solution might put your security at risk in a discussion with Justin Beals and Sam Oberholtzer.
January 25, 2022
Blog
What is a bridge letter in a SOC 2 report?
A bridge letter is a document made available by vendors to cover a period of time between the reporting period end date of the current SOC report and the release of a new SOC report.
January 19, 2022
Blog
Processes, policies and controls: what's the difference?
Justin Beals joins Sam Oberholtzer to discuss cybersecurity controls, policies, and processes. Learn more about building a valuable cybersecurity posture.
January 11, 2022
Blog
Entrepreneurial itch to enterprise software: how Strike Graph came to be
Justin Beals and Brian Bero share how an entrepreneurial itch and fascination with technology led them to focus their efforts on cybersecurity.
January 04, 2022
Blog
3 easy ways to keep calm and stay focused during audit season
Justin Beals joins ex-auditor Sam Oberholtzer for a conversation about how to reduce compliance burnout, even during a busy audit season.
December 22, 2021
Blog
Why trust assets are essential to growing your business
Trust assets are the most effective way to build trust with customers and help speed along the sales process proving your security compliance achievements.
November 17, 2021
Blog
HIPAA + SOC 2: Why tackling them in unison makes sense
Strike Graph's flexible platform makes it easier to achieve HIPAA and SOC 2 compliance. Learn how we can help you tackle both simultaneously.
November 03, 2021
Podcast
When Federal Agents Ignore Court Orders: What Happens to Democracy? | Secure Talk with Claire Finkelstein
Secure Talk Episode:When Federal Agents Ignore Court Orders: What Happens to Democracy? | Secure Talk with Claire Finkelstein
February 10, 2026
Podcast
Shared Wisdom: Why AI Should Enhance Human Judgment, Not Replace It | Secure Talk with Alex Pentland
Secure Talk Episode:Shared Wisdom: Why AI Should Enhance Human Judgment, Not Replace It | with Alex Pentland
January 27, 2026
Podcast
The 2026 Planning Episode: 5 key security imperatives.
Secure Talk Special Episode: The 2026 Planning Episode: 5 key security imperatives.
January 13, 2026
Podcast
Secure Talk Special Episode: Building Secure Societies in the Age of Division: The Seven Lessons for Humanity Heading Into 2026
Secure Talk Special Episode: Building Secure Societies in the Age of Division: The Seven Lessons for Humanity Heading Into 2026
December 30, 2025
Podcast
Building a Thriving Future: AI Ethics & Security in Virtual Worlds | Dr. Paola Cecchi - Dimeglio
Secure Talk Episode: Building a Thriving Future: AI Ethics & Security in Virtual Worlds | Dr. Paola Cecchi - Dimeglio
December 16, 2025
Podcast
Why Security Leaders Struggle With Security Culture | Steven Sloman on SecureTalk
Secure Talk Episode: Why Security Leaders Struggle With Security Culture | Steven Sloman on SecureTalk
December 02, 2025
Podcast
From Punk Rock Anarchist to Bank Security Leader: An Unlikely Journey in Threat Intelligence | SecureTalk with Joe Rossi
Secure Talk Episode: From Punk Rock Anarchist to Bank Security Leader: An Unlikely Journey in Threat Intelligence | SecureTalk with Joe Rossi
November 18, 2025
Podcast
Inside CMMC Implementation: What November 10th Means for Defense Contractors | Secure Talk with Bob Kolasky
A Secure Talk Episode: Inside CMMC Implementation: What November 10th Means for Defense Contractors | Secure Talk with Bob Kolasky
November 04, 2025
Podcast
Beyond Big Cities: Understanding Cybersecurity in Mid-Sized Communities | Secure Talk with Lars Kruse
A Secure Talk Episode:Beyond Big Cities: Understanding Cybersecurity in Mid-Sized Communities | Secure Talk with Lars Kruse
October 21, 2025
Podcast
Preparing for the Quantum Era: Why Blockchain is Leading the Charge | James Stephens
A Secure Talk Episode: Preparing for the Quantum Era: Why Blockchain is Leading the Charge | James Stephens
October 07, 2025
Podcast
Breaking Cybersecurity's 12 Hidden Paradigms: A Futurist's Guide to Security Evolution with Heather Vescent
A Secure Talk Episode:Breaking Cybersecurity's 12 Hidden Paradigms: A Futurist's Guide to Security Evolution with Heather Vescent
September 23, 2025
Podcast
AI Coding Hype vs Reality: The 2025 AI Code Security Report with Chris Wysopal
A Secure Talk Episode:The Invisible Majority: AI Coding Hype vs Reality: The 2025 AI Code Security Report with Chris Wysopal
September 09, 2025
Podcast
The Invisible Majority: How Social Media Erases 90% of Voices | Dr. Claire Robertson
A Secure Talk Episode:The Invisible Majority: How Social Media Erases 90% of Voices | Dr. Claire Robertson
August 26, 2025
Podcast
An Identity Crisis: How AI Agents Are Redefining Enterprise Security | with Rishi Bhargava
A Secure Talk Episode: An Identity Crisis: How AI Agents Are Redefining Enterprise Security | with Rishi Bhargava
August 12, 2025
Podcast
The Insider Threat: How a US Soldier Planned for Years to Kill His Own Unit with Bart Womack
A Secure Talk Episode: The Insider Threat: How a US Soldier Planned for Years to Kill His Own Unit"
July 29, 2025
Podcast
Machines Running Amok: We've Created More Than We Can Secure | Oded Hareven
A Secure Talk Episode:Machines Running Amok: We've Created More Than We Can Secure | Oded Hareven
July 15, 2025
Podcast
Open Source vs Commercial: How "Winning Culture" Has Made Us More Vulnerable | Greg Epstein
A Secure Talk Episode: Open Source vs Commercial: How Winning Culture Has Made Us More Vulnerable | Greg Epstein
July 08, 2025
Podcast
Securing AI at Enterprise Scale: Lessons from Walmart's Transformation with Tobias Yergin
A Secure Talk Episode: Securing AI at Enterprise Scale: Lessons from Walmart's Transformation with Tobias Yergin
July 01, 2025
Podcast
Special Episode: The Secure Talk Security Awareness Training 2025 (With HIPAA!)
A Secure Talk Episode: The Secure Talk Security Awareness Training 2025 - Special Episode (With HIPAA!)
June 24, 2025
Podcast
The Security Leader Who Predicted AI Would Replace His Own Team (And Why He's Right) with Satyam Patel
A Secure Talk Episode: The Security Leader Who Predicted AI Would Replace His Own Team (And Why He's Right) with Satyam Patel
June 17, 2025
Podcast
Can Cybersecurity be “Agile”? with Brian Wagner
A Secure Talk Episode: Can Cybersecurity be "Agile"? With Brian Wagner
June 10, 2025
Podcast
The AI Creator's Confession: "I Built Google Translate to Unite People. It's Now Tearing Us Apart" with De Kai
A Secure Talk Episode:The AI Creator's Confession: "I Built Google Translate to Unite People. It's Now Tearing Us Apart" with De Kai
June 03, 2025
Podcast
Securing Society Through Data Kindness: How Cooperation Becomes Our Best Defense with Aram Sinnreich and Jesse Gilbert
A Secure Talk Episode: Securing Society Through Data Kindness: How Cooperation Becomes Our Best Defense with Aram Sinnreich and Jesse Gilbert
May 27, 2025
Podcast
The Quantum Security Precipice: Why Michele Mosca is Building Cryptographic Resilience Before It's Too Late
A Secure Talk Episode: The Quantum Security Precipice: Why Michele Mosca is Building Cryptographic Resilience Before It's Too Late
May 20, 2025
Podcast
National Security in Crisis: How Geopolitical Chaos Threatens Cybersecurity & Democracy with Mike LeFever
A Secure Talk Episode: National Security in Crisis How Geopolitical Chaos Threatens Cybersecurity & Democracy" Secure Talk with Mike LeFever
May 13, 2025
Podcast
How Russian Disinformation Networks Are Poisoning AI Chatbots | SecureTalk with NewsGuard Experts
A Secure Talk Episode: How Russian Disinformation Networks Are Poisoning AI Chatbots | SecureTalk with NewsGuard Experts McKenzie Sadeghi and Isis Blachez
May 06, 2025
Podcast
Inventing Threat Intelligence: The Story Behind Eldon Sprickerhoff's startup success
A Secure Talk Episode: Inventing Threat Intelligence: The Story Behind eSentire's Success with Eldon Sprickerhoff
May 01, 2025
Podcast
The Future of APIs in the Age of AI Agents: A Conversation with Postman
In this episode of SecureTalk, host Justin Beals explores the evolving world of API technology and security with Sam Chehab, Head of Security at Postman
May 01, 2025
Podcast
Beyond the Blinky Lights: Why Security Governance Drives Technology
In this eye-opening episode of SecureTalk, host Justin Beals welcomes Bryant Tow, Chief Security Officer at LeapFrog Services, to discuss why technology
April 22, 2025
Podcast
From Burning Servers to Enterprise Resilience The Evolution of Internet Security With Akamai
In this eye-opening episode of SecureTalk, host Justin Beals welcomes Joe Gronemeyer, Solutions Engineer at Akamai Technologies, for a masterclass in how
April 15, 2025
Podcast
"There's No Such Thing as Crypto Crime": Nick Furneaux on Blockchain Investigation, Digital Forensics, and the Future of Cryptocurrency
A Secure Talk Episode: There's No Such Thing as Crypto Crime:Nick Furneaux on Blockchain Investigation, Digital Forensics, and the Future of Cryptocurrency
April 08, 2025
Podcast
Hijacking AI Memory: Inside Johann Rehberger's ChatGPT Security Breakthrough
In this eye-opening episode of SecureTalk, host Justin Beals interviews Johann Rehberger, a seasoned cybersecurity expert and Red Team Director at
April 01, 2025
Podcast
Predicting Data Breach Risk: How Mathematical Privacy Is Revolutionizing Data Sharing with Simson Garfinkel
A Secure Talk Episode: Predicting Data Breach Risk: How Mathematical Privacy Is Revolutionizing Data Sharing with Simson
March 25, 2025
Podcast
The Future of CMMC: Surviving the new Federal Security Landscape with Former NRMC Director Bob Kolasky
In this critical episode of SecureTalk, host Justin Beals sits down with Robert Kolasky, former founding director of the National Risk Management Center at
March 18, 2025
Podcast
Redefining Personhood: The Legal and Ethical Challenges of an Advanced General Intelligence with James Boyle
A Secure Talk Episode: Redefining Personhood: The Legal and Ethical Challenges of an Advanced General Intelligence with James Boyle
March 11, 2025
Podcast
How do you get 10,000 Developers to write Secure Code? with Dimitry Shvartsman
A Secure Talk Episode: How do you get 10,000 developers to write secure code? with Dimitry Shvartsman
March 04, 2025
Podcast
AI Therapy: Should we believe Silicon Valley's Bold Claim at Solving
A Secure Talk Episode: AI Therapy: Should We Believe Silicon Valley's Bold Claim at Solving Mental Health? With Daniel Oberhaus
February 25, 2025
Podcast
From Arab Spring Frontlines to Cybersecurity Frontiers: A Naval Officer's Journey with Terence Bennett
Terence Bennet watched from the deck of the USS Paul Hamilton as the Arab Spring unfolded. As a naval officer, he realized that his battlefield awareness
February 18, 2025
Podcast
The AI wars and what DeepSeek means to AI and security
A Secure Talk Episode: The AI wars and what DeepSeek means to AI and security
February 11, 2025
Podcast
What Matters Next: Decision Making in a Rapidly Changing World with Kate O'Neill
In this episode of Secure Talk, host Justin Beals welcomes Kate O'Neill, a passionate tech humanist dedicated to crafting technology solutions that
February 04, 2025
Podcast
Unveiling the Secrets of Cryptography with Panos Louridas: Early Computing, Encryption, and Modern Challenges
In this episode of SecureTalk, host Justin Beals warmly welcomes Panos Louridas for an insightful discussion on the history, evolution, and future of
January 28, 2025
Podcast
From botnets to AI health: Michael Tiffany’s mission to empower personal data sovereignty
In 2000 the internet was expanding at an astronomical rate. Consumers were logging in via dial-up modems by the hundreds of millions and businesses were
January 21, 2025
Podcast
Cryptography, quantum computing, and the future of security with Dr. Bill Anderson
A Secure Talk Episode: Inventing Threat Intelligence: Cryptography, Quantum Computing, and the Future of Security with Dr. Bill Anderson
January 14, 2025
Podcast
The Cybersecurity Maturity Model (CMMC) has arrived! with Stephen Ferrell
A Secure Talk Episode: The Cybersecurity Maturity Model (CMMC) has arrived! With Stephen Ferrell.
December 17, 2024
Podcast
Unlocking AI’s potential privately, safely and responsibly with Dan Clarke
A Secure Talk Episode: Unlocking AI’s Potential Privately, Safely and Responsibly with Dan Clarke
December 10, 2024
Podcast
Innovative approaches to cyber security awareness training with Craig Taylor
A Secure Talk Episode: Innovative Approaches to Cyber Security Awareness Training with Craig Taylor
December 03, 2024
Podcast
The Evolution of Identity Management with Eric Olden
In this episode of SecureTalk, we discuss the evolution of identity management with Eric Olden, co-founder and CEO of Strata Identity. Identity Management
November 26, 2024
Podcast
Fairy tales and firewalls: bridging myths with modern security with Luca Vigano
A Secure Talk Episode:Fairy Tales and Firewalls: Bridging Myths with Modern Security with Luca Vigano
November 19, 2024
Podcast
Application Security Management and the new SBOM with Idan Plotnik
In this episode of SecureTalk, host Justin Beals speaks with Idan Plotnik, co-founder and CEO of Apiiro, about the complexities of application
November 12, 2024
Podcast
Privacy reforms we need now with James B.Rule
A Secure Talk Episode: Privacy reforms we need now with James B. Rule
November 05, 2024
Podcast
Is technology a religion? with Greg Epstein
A Secure Talk Episode: Is Technology a Religion? with Greg Epstein
October 29, 2024
Podcast
Enterprise security from healthcare to GE: accountability, strategy, and value creation with Bob Chaput
A Secure Talk Episode: enterprise security from healthcare to GE: accountability, strategy, and value creation with Bob Chaput
October 22, 2024
Podcast
Forging the future of security with Rey Kirton at Forgepoint Capital
In the never-ending vortex of Silicon Valley's hype cycle, it's easy to get lost in the sea of superficial success stories and forget that true innovation
October 15, 2024
Podcast
Ethics and innovation in medical AI: a conversation with Dr. Paul Campbell.
A Secure Talk Episode: Ethics and innovation in medical AI: a conversation with Dr. Paul Campbell."
October 08, 2024
Podcast
Cyber warfare and national cyber defense with Jason Healey
A Secure Talk Episode: "Cyber warfare and national cyber defense with Jason Healey."
October 01, 2024
Podcast
Mastering Cyber Shadows: Alex Cox's take on LockBit's resilience and the role of threat intelligence
A Secure Talk Episode: Mastering Cyber Shadows: Alex Cox's take on Lockbit's resilience and the role of threat intelligence
September 28, 2024
Podcast
Making Security a Part of Product Development with Naomi Buckwalter
I’ve participated or led technology product teams for 25 years. And engaging in effective security practices was three simple activities: least privileges,
September 24, 2024
Podcast
From Cryptography to Web 3 powered by Blockchain with David Holtzman
The state of networked computing systems today relies heavily on a networking architecture designed and implemented by people like David Hotlzman
September 17, 2024
Podcast
Beyond the Ballot: Election Security Insights with Mark Listes
A Secure Talk Episode: The Human toll of jobs/security with Danny Goodwin and Edward Schwarzschild
September 10, 2024
Podcast
The Human Toll of Jobs / Security with Danny Goodwin & Edward Schwarzschild
A Secure Talk Episode: The Human toll of jobs/security with Danny Goodwin and Edward Schwarzschild
September 03, 2024
Podcast
Hack to learn: integrating humanities into cybersecurity with Dr. Aaron Mauro
A Secure Talk Episode: Hack to learn: Integrating humanities into Cybersecurity with Dr. Aaron Mauro
August 27, 2024
Podcast
Hacking the Human OS: Insights from Social Engineering expert Christopher Hadnagy
A Secure Talk Episode: Hacking the human OS: Insights from Social Engineering expert Christopher Hadnagy
August 23, 2024
Podcast
The Algorithmic Mirror: Reflecting data's role in modern life
A Secure Talk Episode: The Algorithmic mirror: reflecting on data's role in modern life with Aram Sinnreich and Jesse Gilbert
August 22, 2024
Podcast
Redefining cybersecurity strategies with Bruce Schneier
A Secure Talk Episode: Redefining cyber security strategies with Bruce Schneier
August 20, 2024
Podcast
Navigating cyber threats: FBI perspectives on protecting business and family with Scott Augenbaum
A Secure Talk Episode: Navigating cyber threats: FBI perspectives on protecting business and family with Scott Agenbaum
August 20, 2024
Podcast
Security threats from the Chrome Web Store with Sheryl Hsu
A Secure Talk Episode: Security Threats from the Chrome Web Store with Sheryl Hsu
August 13, 2024
Podcast
Dynamic data safety: Purandar Das on encryption and beyond
A Secure Talk Episode: Dynamic data safety: Purandar Das on encryption and beyond
August 08, 2024
Podcast
A perfect fit: Using risk to get the right sized security with Christopher Hodson
A Secure Talk Episode: A perfect fit: using risk to get the right sized security with Christopher Hodson
August 07, 2024
Podcast
Mastering the role of CISO with Todd Fitzgerald
A Secure Talk Episode: Mastering the role of CISO with Todd Fitzgerald
August 07, 2024
Podcast
Unraveling the layers of HIPAA: A deep dive into data security with Iliana Peters
In this episode of SecureTalk, host Justin Beals, CEO of StrikeGraph, discusses the complexities of HIPAA, data privacy, and healthcare security
August 06, 2024
Podcast
Hacking a nation: Alejandro Caceres' bold attack on North Korea
A Secure Talk Episode: Hacking a Nation: Alejandro Caceres' bold attack on North Korea
August 06, 2024
Podcast
Navigating HIPAA compliance with confidence
A Secure Talk Episode: Navigating HIPAA Compliance With Confidence, with Rebecca Herold and Kevin Beaver
August 05, 2024
Podcast
Cyber threat intelligence: Getting to know the adversary
A Secure Talk Episode: Cyber threat intelligence: Getting to Know the Adversary with Mary D'Angelo
August 02, 2024
Podcast
The #1 vulnerability in cybersecurity is us
A Secure Talk Episode: The #1 Vulnerability in cybersecurity is us with Dr. Abbie Marono
August 02, 2024
Podcast
Crisis fighting: How to plan a successful security incident
A Secure Talk Episode: Crisis Fighting: How to Plan a Successful Security Incident with Mike LeFever and Roderick Jones
August 02, 2024
Podcast
Creating the dark web: How the TOR browser was invented
A Secure Talk podcast episode: Creating the dark web: How the TOR browser was invented with Ben Collier
February 21, 2023
Webinar
Cybersecurity in Medical Devices: Protecting Patient Data and Ensuring Compliance
September 26, 2024
Webinar
Achieving Continuous Compliance How AI and Automation Can Transform Your Program
February 26, 2025
Keep up to date with Strike Graph.
The security landscape is ever changing. Sign up for our newsletter to make sure you stay abreast of the latest regulations and requirements.
Keep up to date with Strike Graph.
The security landscape is ever changing. Sign up for our newsletter to make sure you stay abreast of the latest regulations and requirements.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)

.png?width=2350&height=1260&name=Starter%20Kit%20for%20CMMC%20Plan%20of%20Action%20%26%20Milestones%20(2).png)


.png?width=1200&height=700&name=Blog%20Featured%20Image%20600x350px%20(11).png)

.png?width=1200&height=700&name=Blog%20Featured%20Image%20600x350px%20(10).png)
.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(7).png)
.png?width=600&height=350&name=Blog%20Featured%20Image%20600x350px%20(2).png)




















.png?width=7063&height=1250&name=pl-logo_horizontal%20(1).png)













%20(1000%20x%20600%20px).png?width=1000&height=600&name=G2%20email%20banners%20(1000%20x%20770%20px)%20(1000%20x%20600%20px).png)




.png?width=1251&height=625&name=SEO%20promo%20graphics%20(3).png)



.png?width=2048&height=1433&name=Sales%20Territories%20(1).png)


.png?width=1251&height=625&name=SEO%20promo%20graphics%20(2).png)




-1.png?width=1220&height=722&name=Screenshot%202024-04-11%20at%204_50_25%20PM%20(2)-1.png)
















.png?width=1220&height=524&name=Copy%20of%20Strike%20Graph%20Buttons%20(1).png)































%20(1).png?width=1220&height=560&name=Blog%20Image%20(1220x560)%20(1).png)




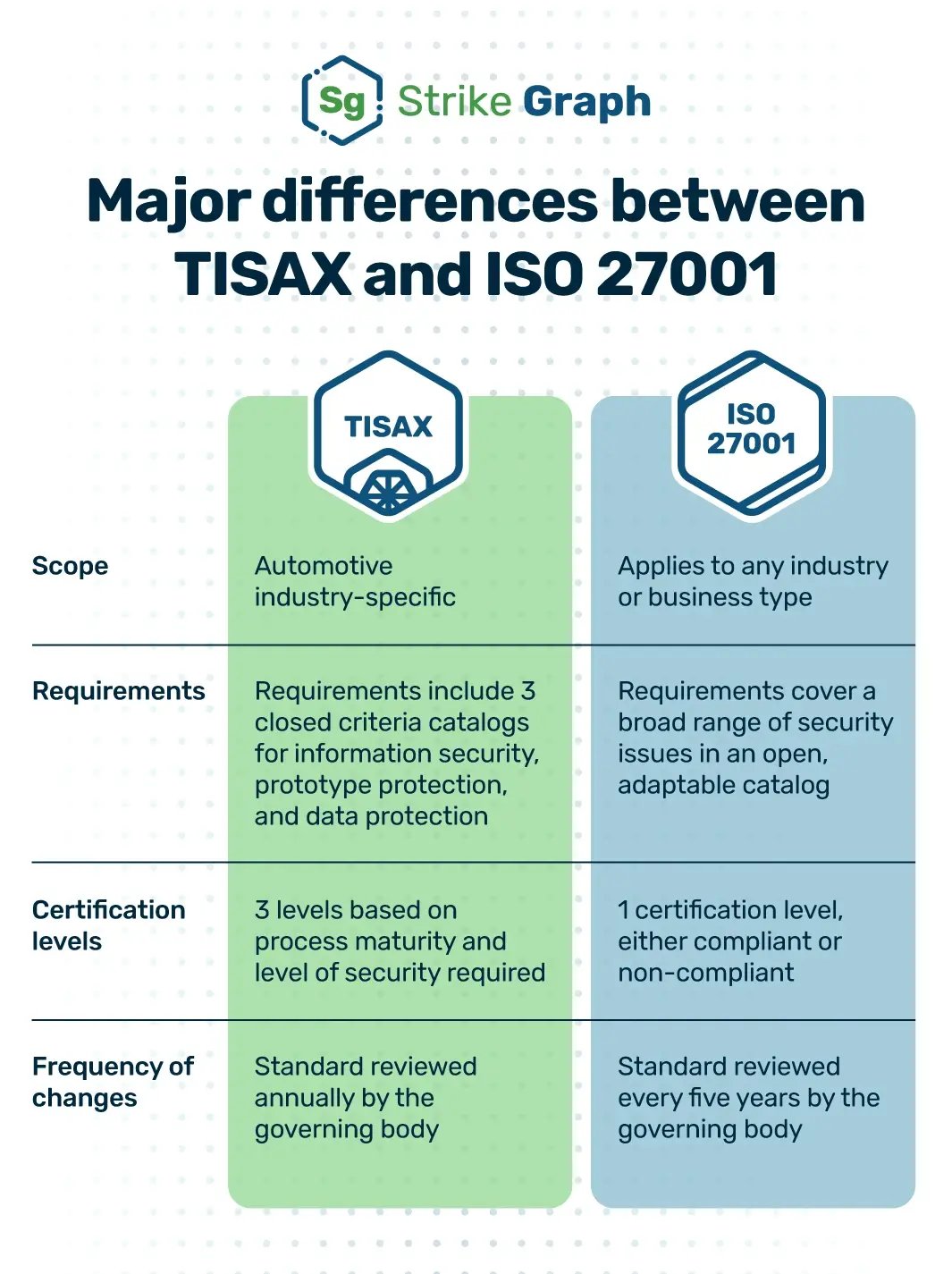



.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(15).jpg)
.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(16).jpg)
.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(17).jpg)
.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(18).jpg)
.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(19).jpg)
.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(20).jpg)
.jpg?width=1220&height=524&name=ezgif_com-gif-maker%20(21).jpg)
.jpg?width=1220&height=560&name=ezgif_com-gif-maker%20(22).jpg)







%20(1)%20(1)%20(1)%20(1)%20(1)%20(1).jpg?width=1220&height=524&name=CPRA-is-here%20(1)%20(1)%20(1)%20(1)%20(1)%20(1)%20(1).jpg)

.webp?width=1220&height=524&name=image%20(7).webp)

.webp?width=1220&height=524&name=image%20(9).webp)






















.png?width=1200&height=515&name=IMG_7147%20(cropped).png)























.jpg?width=600&height=338&name=medium%20(1).jpg)



.jpg?width=600&height=338&name=medium%20(2).jpg)










.png?width=450&height=253&name=2%20(1).png)

































.png?width=1920&height=1080&name=Ep%20215%20Simson%20Garfinlkel%20%20(3).png)





.png?width=1920&height=1080&name=Micah%20and%20Josh%20%20Thumbnail%20(2).png)







-1.png?width=1920&height=1080&name=Video%20Thumbnail%20(2)-1.png)

.png?width=1920&height=1080&name=Video%20Thumbnail%20(2).png)
%20(1).png?width=1920&height=1080&name=Video%20Thumbnail%20(1)%20(1).png)








.png?width=1920&height=1080&name=Video%20Thumbnail_20240903_153835_0000%20(1).png)


.png?width=1920&height=1080&name=Aram%20and%20Jesse%20Thumbnail%20(1).png)
.png?width=1920&height=1080&name=Schneier%20Video%20Thumbnail%20(1).png)



.png?width=1920&height=1080&name=Video%20Thumbnail%20(1).png)




















%20(13).png)
%20(16).png)
%20(19).png)
%20(20).png)
%20(22).png)