Learn the core phases of penetration testing from compliance experts, including tailored approaches for different industries. Explore pen testing timelines and schedules to help you stay on top of each phase and monitor your testing progress effectively.
Key Takeaways:
- Penetration testing follows key phases—pre-engagement, reconnaissance, mapping, vulnerability scanning, exploitation, cleanup, and reporting—each with specific goals and timelines.
- Pen testing usually lasts two to three weeks, but the timeline and activities vary across industries based on technologies, compliance needs, and operational challenges.
- Pen testers use AI to streamline research and enhance reports, but it is still too limited to automate complex or critical aspects of the testing process.
- Effective penetration testing requires a blend of human expertise and technology to address evolving security risks.
What is penetration testing?
Penetration testing, or pen testing, is a security test where experts run a fake cyberattack to uncover weaknesses. It helps organizations find issues, improve defenses, identify security gaps and meet regulatory requirements before real attacks happen. Compliance frameworks like SOC 2 and PCI DSS require pen tests.
Penetration testing phases
Most penetration tests include the same broad phases. They start by defining the scope and pre-engagement rules with the client. Testers gather information during reconnaissance, run vulnerability scans, and attempt to exploit weaknesses. Finally, they clean up traces of their work and deliver a report.
Pen testers use different methods based on the type of system they target, but all follow the same general process. For example, the Penetration Testing Execution Standard (PTES) is a common methodology.
Here's an overview of the main phases in all pen tests, with a general time estimate for each phase in a typical two- to three-week pen testing process. Please note that the timeline varies based on the scale of the test, the environment, and the client's needs.
- Pre-engagement phase (2-3 days)
In the pre-engagement phase, the team collaborates with the client to define the test's scope, goals, and objectives. They identify which systems to test, set timelines, and plan logistics. This phase ensures both sides are on the same page, prevents the pen testers from disrupting the system, and includes completing legal documents that protect the testers and the organization.
- Reconnaissance phase (4-6 days)
In this phase, the pen testing team gathers as much information as possible about the target. This includes publicly available data (Open Source Intelligence or OSINT) and other relevant information. Depending on the scope, teams run passive reconnaissance (using public sources) and active reconnaissance (interacting directly with the system).
- Mapping (1-2 days)
The team creates a detailed system map to identify potential entry points. They use asset mapping and discovery scanning methods to identify and map all active devices, services, and systems within a target network. The map shows how the systems connect and reveals the most vulnerable areas.
- Vulnerability scanning: (2-3 days)
Using the data from reconnaissance and mapping, testers run vulnerability scans to find weak points. They manually verify scan results to confirm which vulnerabilities to target during the test.
- Exploitation phase (1-3 days)
The team attempts to exploit the identified vulnerabilities to simulate a real cyberattack. Depending on the weaknesses, testers use various techniques to gain unauthorized access and demonstrate how a malicious hacker could access the client's system.
- Clean Up (1-2 days)
The team removes all traces of the simulated attack to prevent real hackers from using the same vulnerabilities.
- Reporting (2-4 days)
In this step, the team prepares a detailed report outlining the vulnerabilities they found, how they exploited them, and recommendations to strengthen the system.
![Blog Graphic [SEO_pen-test-phases-SG blog]](https://www.strikegraph.com/hs-fs/hubfs/Blog%20Graphic%20%5BSEO_pen-test-phases-SG%20blog%5D.webp?width=248&height=816&name=Blog%20Graphic%20%5BSEO_pen-test-phases-SG%20blog%5D.webp)
Steps in penetration testing
Each phase of penetration testing includes important steps. Testers define the scope and set rules with the client on what to test and when. They run targeted vulnerability scans based on the client's needs and use the results to guide their exploitation efforts.
Steps in pre-engagement
In the pre-engagement phase, the client and pen testing team agree on the scope, timeline, and targets. They also draft rules of engagement and address legal or ethical requirements. This phase can be time-consuming and usually isn't included in the formal pen testing timeline.
Here's an overview of the key steps in the pre-engagement phase:
- Scope the test
Defining the scope of the pen test is one of the most critical steps. The client and testing team work together to decide which systems the testers will target, which areas to exclude, and whether the testing will occur in production or staging environments.
 "Scoping is when we work with the client to decide which parts of the system we're going to try to exploit," explains Micah Spieler, Chief Product Officer at Strike Graph. "Are we testing APIs, websites, or both? And will it happen in the staging environment or in production? Most customers stick to a predefined playbook for testing, but some go for more custom, rigorous tests."
"Scoping is when we work with the client to decide which parts of the system we're going to try to exploit," explains Micah Spieler, Chief Product Officer at Strike Graph. "Are we testing APIs, websites, or both? And will it happen in the staging environment or in production? Most customers stick to a predefined playbook for testing, but some go for more custom, rigorous tests."
The scoping phase also helps the pen testers get industry-specific information they need from clients that will help them perform a more accurate and useful test.
 "One of the most important questions I ask when scoping with a client is, 'What do you consider a critical finding?'" says Max Turner, the Pen Testing Lead at Red Sentry. "Some industries treat certain findings as critical that wouldn't be obvious to someone outside the field. Scoping gives the client a chance to explain which information needs the most protection and highlight anything else we need to know. This process gives us the context to design a thorough test that aligns with the client's needs and priorities."
"One of the most important questions I ask when scoping with a client is, 'What do you consider a critical finding?'" says Max Turner, the Pen Testing Lead at Red Sentry. "Some industries treat certain findings as critical that wouldn't be obvious to someone outside the field. Scoping gives the client a chance to explain which information needs the most protection and highlight anything else we need to know. This process gives us the context to design a thorough test that aligns with the client's needs and priorities."
- Draft rules of engagement
Testers use rules of engagement to set clear boundaries and protect both the client and their own team. For example, the client and testing team will decide whether the test will be a black box test or a gray box test. In black box pen testing, the tester doesn't receive any internal knowledge of the system. This test simulates the perspective of an external attacker, who only relies on publicly available information to identify vulnerabilities. In gray box pen testing, the tester has some access to the system. This test simulates an attack from an insider or a compromised user.
 "These documents outline exactly where and when we can access the client's systems," says Steven Casey, Associate Penetration Tester at Strike Graph. "They also list emergency contacts in case our work affects a web application or server, especially during business hours. This ensures we can address any issues quickly and minimize disruption."
"These documents outline exactly where and when we can access the client's systems," says Steven Casey, Associate Penetration Tester at Strike Graph. "They also list emergency contacts in case our work affects a web application or server, especially during business hours. This ensures we can address any issues quickly and minimize disruption."
"We also inform customers about the general timeframe for the penetration testing," explains Spieler. "That way, if they notice any unusual activity, they know it's us and don't start ringing alarm bells."
- Set objectives and methodologies
The pre-engagement phase will set objectives based on the client's needs, including compliance requirements. Some pen testing teams also dive into their methodologies with the client, but that's rare.
"Most pen testing teams follow a well-defined methodology and rarely deviate from it unless a specific use case requires it," Turner explains. "This consistency benefits clients because, while we're always willing to walk them through our process, the person on-call is often focused on meeting compliance requirements and may not have the technical background to assess different methods. In these situations, our explanations provide reassurance that we have a precise plan."
- Sign legal agreements
Before allowing a team into their network, clients usually have the pen testers sign an NDA, or non-disclosure agreement. The two parties will also sign other legal documents to protect both sides.
Casey highlights that it's in the pre-engagement phase when they get written permission and sign any necessary legal documents to ensure the pen testing team doesn't get in trouble. "One key difference between a pen tester and a malicious actor r is that we have signed, written permission to perform the tests we're conducting. These documents fundamentally protect both sides — we don't get in trouble for hacking, and they're safeguarded from significant impacts to their system."
Steps in the reconnaissance phase
In the reconnaissance phase, testers research the target to understand the system and its potential vulnerabilities. They collect publicly available data and research employee behavior. This phase guides the next stages of the test and is the most time-consuming part of pen testing.
Here's an overview of the key steps in the reconnaissance phase:
- Gather OSINT (open-source intelligence)
"One of the first things we do is visit the client's landing page," explains Turner. "We read their blogs and scour their website to see if they have given us any 'free passes,' or publicly available information that might be sensitive and that we could use to exploit their system."
- Conduct active gathering
In this step, testers interact with the target to uncover specific details. They might explore open systems, analyze which services are running, or engage directly with servers to identify potential weak spots.
- Do social engineering research
Testers also investigate employee behaviors and public activities to prepare for phishing or other social engineering attacks. For example, a tester might try to trick employees into interacting with a fake landing page or mimic password reset emails. This step helps testers assess how likely employees are to reveal sensitive information.
Steps in the mapping phase
In the mapping phase, pen esters use information from reconnaissance to map the target system's structure and find weaknesses. They outline connections and pinpoint potential entry points. This phase helps testers create a clear plan for targeted attacks in the next pen testing phase.
"In the mapping phase, you're learning how the application works," explains Casey. "We identify the systems, networks, applications, and anything else in the target environment and map them out to see how they interact, and where we could possibly enter."
Here's an overview of the main steps in the mapping phase:
- Create system maps
In mapping, the tester will take the network and map it out so they can see how hosts are connected and understand the basic structure of the target.
- Map attack vectors
Mapping includes studying system relationships to understand how an attacker could move from one system to another. Testers identify high-risk areas, such as unprotected services or overlooked subdomains, that could become entry points.
Steps in vulnerability scanning
During vulnerability scanning, testers use automated tools to find possible weaknesses in the system. They manually check the results to confirm issues and focus on high-risk ones. This step helps testers target the most important vulnerabilities in the next phase.
Vulnerability scans are common, automated tools that many organizations run regularly to perform a vulnerability analysis that helps them identify potential weaknesses. Although vulnerability assessments are an important part of pen testing, vulnerability scans differ significantly from a full penetration test.
Spieler explains the difference: "Penetration testing definitely includes vulnerability scanning, but they aren't the same thing. Vulnerability scanning is automated — it finds known vulnerabilities and tries to exploit them. Pen testing, though, involves an expert going deeper. It's not just about what the scans find; it's about what a human can verify and exploit beyond what the scans show."
Here's an overview of the steps in vulnerability scanning:
- Run the initial scan
Testers use automated tools to scan the target system for weaknesses, such as outdated software or open ports. The tool the tester uses depends on the type of system the scanner is testing. For example, there are common network scanning tools, application scanning tools, database scanning tools, and more. Each tool will return a list of potential vulnerabilities for the specific system.
- Analyze the scan results and verify
"Scanners often return false positives — issues that the scan detects as a vulnerability but don't actually pose a threat," explains Casey. "It’s our job to ensure the vulnerability is real. For instance, if a scanner flags an outdated version of web server software, we verify it, look up the vulnerability, and follow the steps to confirm the issue.”
Manual testing ensures the vulnerabilities identified are exploitable. "A pen tester might explore parameters like URLs or form fields and inject payloads to see how the application handles input," Casey adds.
- Prioritize vulnerabilities
Testers prioritize vulnerabilities based on their potential impact, ease of exploitation, and relevance to the test’s scope. They focus on high-risk vulnerabilities for the next phase of testing. Throughout the process, testers ensure they follow the rules of engagement by avoiding exploits that could disrupt the system significantly. They might also start rescanning for vulnerabilities as a final confirmation.
“If we identify a vulnerability that will significantly disrupt the system, like compromising a landing page, we will note it in the report, but we won’t actively exploit it," says Turner.
Steps in the exploitation stage
In the exploitation phase, pen testers use the information they gathered to hack target systems. They simulate real-world attacks to show how a real hacker could gain unauthorized access. This phase lasts a day or two to limit how long the testers are in the system.
The steps in exploitation vary significantly based on the environment, but the goal is to move away from identifying vulnerabilities to demonstrate actual risks.
Here's an overview of the steps in the exploitation phase:
- Prepare exploitation
“When we’re in the exploitation phase, we use information from the earlier phases – reconnaissance, mapping, and vulnerability scanning – to make a plan of attack,” says Turner. “Then, we’ll develop or customize tools and payloads to exploit specific weaknesses.”
- Execute the exploits
Testers launch targeted attacks over a day or two to see if they can use vulnerabilities to access systems, applications, or networks.
- Escalate
If successful, testers document how they gained access and determine how far they can penetrate the system. They may escalate privileges or move laterally to assess the full scope of the risk and explore additional vulnerabilities within the environment.
Steps in the cleanup phase
In the cleanup phase, testers remove all traces of the test to prevent attackers from exploiting them. They delete tools, scripts, or payloads and return the system to its original state. This step ensures the system remains secure and operates like it did before the pen test.
The cleanup and reporting phase make up the post-exploitation pen testing activities. Here’s an overview of the steps in the cleanup phase:
- Remove tools and artifacts
"The cleanup phase is crucial because we make sure we don’t leave any openings for a malicious hacker,” says Casey. “We uninstall tools, delete counts, clear logs, close ports, and otherwise return the system as it was before we entered. There should be absolutely no trace of our presence.”
- Restore system configurations
Testers restore any system settings, accounts, or configurations changed during the test to ensure the system functions normally.
- Collect final documentation
Turner emphasizes the importance of gathering all necessary documentation before completing the cleanup. “It’s your chance for a final check to make sure you have good evidence — like screenshots — before you remove any trace of that evidence,” he explains.
Steps in the reporting phase
In the reporting phase, the testers write a report summarizing what they did during the pen test and their results. Usually, the tester offers broad recommendations but doesn’t go into detail on how to resolve any issues. The report’s depth and detail vary based on the testing team’s approach.
Although the reporting phase is the final step in the penetration test, Turner explains that the report comes together throughout the entire process. “As the pen tester works, they’re taking screenshots, writing notes, copying scripts, and otherwise documenting their process,” he says. “Then, after they’ve finished cleaning up from the test, they compile everything into a report that summarizes the test.”
The details of the pen testing report vary based on the testing team and the client’s needs. Here’s a broad overview of the steps most pen testing companies will take to draft a report:
- Write a high-level summary for executives
This section offers a concise overview of key findings and highlights major concerns. It provides broad recommendations to help non-technical staff, like the CEO, understand what’s wrong and who can help address the issues.
- Present a detailed walk-through of methodology findings
Pen testers present vulnerabilities in the order they discovered them, often with screenshots to demonstrate the findings. They describe how they identified the issues and which tools they used.
- Write technical documentation
Most reports list the exact commands, tools, and scripts the pen tester used. Sometimes, they’ll include instructions so the client’s technical team can replicate the results.
- Make remediation recommendations
Most reports provide general recommendations rather than step-by-step fixes. “We give general recommendations, like ‘close this port’ or ‘restrict access to this server,’ but we don’t tell them exactly how to fix every issue,” explains Spieler. “The client’s internal security team knows their system best and is in the best position to implement the solutions.”
Penetration testing timeline
![Blog Graphic [SEO_pen-test-timeline-SG blog]](https://www.strikegraph.com/hs-fs/hubfs/Blog%20Post%20Images/Blog%20Graphic%20%5BSEO_pen-test-timeline-SG%20blog%5D.webp?width=460&height=965&name=Blog%20Graphic%20%5BSEO_pen-test-timeline-SG%20blog%5D.webp)
Penetration testing schedule template
Use our penetration testing schedule template to plan and track your next penetration test. It includes all major penetration tests to help you organize phases, set milestones, and track progress.
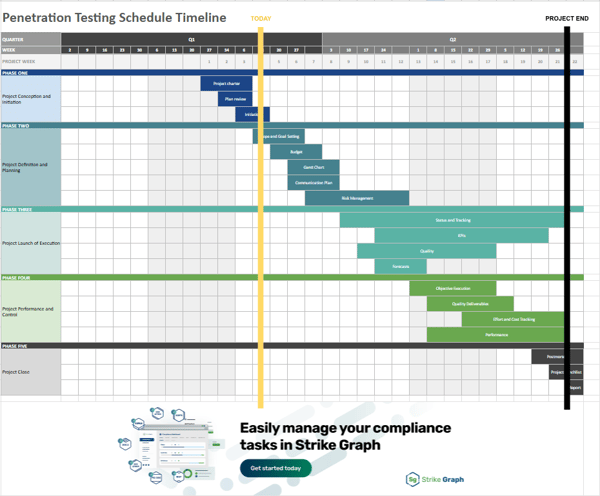
Download the pen testing timeline template now to help plan your security efforts.
How pen testing process varies by industry
The pen testing process varies based on different technologies and rules in various industries. For example, testers use different methods to address tech and compliance needs in fintech vs. healthcare. Each has unique concerns.
“The general flow of a penetration test doesn’t vary too much,” says Turner. “We begin with pre-engagement, gather information, run vulnerability scans, exploit the system, clean up, and finish with a report summarizing our findings. However, how we approach each step can vary significantly based on the client’s industry. Each sector has its own type of sensitive data, technology operational challenges, and compliance needs. All that means is that the goals might change, which will affect the details like which scans we run, how long each step takes, and where in the environment we focus our efforts.”
Here's a summary of some of the unique considerations for major sectors:
-
- Unique technologies:
“Since APIs are such a big part of fintech, they shape how we approach the whole process,” Turner explains. “We look for exposed APIs during reconnaissance, scan them for vulnerabilities, and, if we find weaknesses, we try to exploit them to see how they could impact the system.”
-
- Data sensitivity
Because financial data is very sensitive, testers must navigate specific file restrictions. “Even though we’re under an NDA, we still get instructions like ‘Please don’t open this file’ or ‘don’t access these accounts,’ and we will work around those needs,” adds Turner.
-
- Operational challenges
Fintech companies operate continuously, limiting the availability for testing. Testers need to coordinate schedules carefully to avoid disrupting services.
-
- Compliance needs
“Fintech companies are understandably laser-focused on Payment Card Industry Data Security Standard (PCI DSS) compliance, which has the most strict penetration testing requirements,” Turner says.
-
- Unique technologies
Healthcare systems rely on legacy technology that is often outdated but critical to daily operations.
“We can turn legacy systems inside out — they’re wide open,” Turner says. “But that’s precisely the problem. We usually have to recommend replacing the machine or software or seriously limiting access, sometimes to just one person. These are enormous tasks for anyone to take on, let alone a healthcare organization that’s usually running continuously and doesn’t have much time to replace or ramp up legacy systems.”
-
- Data sensitivity
Healthcare's focus on PHI (Protected Health Information) significantly impacts scoping, data handling, and reporting during penetration testing. The pen tester must ensure their test aligns with Health Insurance Portability and Accountability Act (HIPAA) regulations and safeguards patient data while identifying vulnerabilities.
“PHI impacts every part of the process,” says Turner. “During scoping, we prioritize systems that contain PHI. We handle data carefully to avoid exposure, even during testing, and in the report, we make sure to clearly document any findings involving PHI vulnerability to comply with HIPAA regulations.”
-
- Compliance needs
Healthcare organizations must meet both HIPAA and FDA regulations.
“We always operate with our client's best interest in mind, and that includes double-checking compliance needs,” adds Turner. “For example, we may at times remind healthcare clients that we need to run specific tests to make sure they meet FDA approval. These security requirements can be difficult to understand even for clients that are neck-deep in the sector.”
- Technology (IT and software)
-
- Unique technologies
IT companies often have diverse technology stacks with uncommon or outdated tools, making testing complex.
Turner says the tech sector usually runs the most diverse networks and systems. “There’s a lot of variance in tech stacks. Some small companies use rare technologies that make testing challenging,” he says. “Sometimes we even see a ‘homemade’ solution which can be an interesting challenge, but certainly makes us deviate from the traditional playbook.”
-
- Data sensitivity
IT companies may not directly manage sensitive data but often store or process large volumes of client data, requiring careful handling and proper scoping to avoid data breaches.
-
- Operational challenges
Many IT companies rely on third-party vendors, adding complexity to the scoping phase.
“In one example, a client asked us to test an application, but they either didn’t realize the application relied on third-party processes that they didn’t own or did not think it would present a problem,” says Turner. “That created issues because they didn’t have the right to test it. As you might imagine, the actual owner of that property might have something to say about us attempting to hack it.”
Ensuring ownership and permissions for third-party software becomes essential to avoid testing roadblocks.
-
- Compliance needs
IT companies often align with frameworks like SOC 2 or ISO 27001, which have specific requirements for penetration testing that the tester must follow.
- Government sector
- Unique technologies
Government agencies sometimes rely on custom-built tools and niche technologies that can make pen testing more complex. Testers must adapt to specific technologies that aren’t common in other industries.
- Data sensitivity
Government agencies handle sensitive and classified data and have strict data sovereignty rules.
“Government contracts require US-based testers, and sometimes they need everyone on the team to have security clearance,” explains Turner. “This limits who can participate and requires careful vetting of personnel.
- Operational challenges
Background checks and security clearances are often required for testers and anyone involved in the project.
“A lot of administrative and security clearance tasks that have nothing to do with pen testing can eat up project time if you’re not aware of them,” explains Turner. These administrative hurdles can significantly delay testing timelines.
-
- Compliance or other security needs:
Government testing heavily focuses on high-level threat simulations to assess resilience against advanced persistent threats (APTs). There is also more emphasis on social engineering, testing defenses against phishing and insider threats.
How will AI impact the penetration testing process?
AI will impact penetration testing by automating parts of the process and making it more efficient. It will improve tests like vulnerability scans, help with research and reports, and generate code. However, it can’t fully automate the process yet, and using AI raises concerns about sharing sensitive data.
How has AI already changed the pen test process?
Many pen testers use AI to improve reports, research client systems, and handle basic communication like drafting emails. Some use AI to create scripts or help with social engineering simulations. However, the technology isn’t advanced enough to fully automate manual hacking or complex tasks.
Today, most pen testers use AI to help with language-related tasks, like writing emails and reports. Some experts say they sometimes use AI to write scripts, but the tech is still limited.
“I use AI for common language-related tasks — like making emails more professional or improving reporting templates,” says Casey. “I’ve also experimented with it to help script processes. But AI hasn’t advanced enough yet to significantly improve specialized scans or expedite the technical aspects of penetration testing.”
Turner echoes the benefits but highlights that AI shines the most in the research phase. “I use AI to speed up research, which is arguably the most time-intensive part of the entire process. You need to understand what systems you’re working with, gather information, and connect the dots. If you’re unfamiliar with the tools or environments involved, it’s a steep learning curve. That’s where AI helps the most. It accelerates the process so I can move on to higher-priority tasks.”
He adds that AI has also been helpful for scripting tasks, particularly for recreating public-facing websites in social engineering simulations. “For example, I’ve used AI to create phishing landing pages designed to see if employees will interact with them. Building those manually took a lot of time. But now, I just describe what I need, and AI generates a near-perfect version that I can tweak in minutes. It turns a lengthy task into a quick one, giving me more time to focus on complex work.”
Despite these advantages, Turner remains cautious about AI’s role in penetration testing, particularly when it involves sensitive data. “The intersection of AI and pen testing makes me a bit nervous,” he explains. “Handing over too much control to a machine is risky and could lead to unintended consequences. AI is already expanding the reach of hacking, especially in social engineering, where these tactics are becoming more accessible. We’re seeing malicious actors using AI to create harmful scripts while posing as ethical hackers. Unfortunately, it’s not hard to bypass the ethical safeguards these tools claim to have. It’s all about asking the right questions the right way.”
How will AI change pen testing in the future?
Artificial intelligence can improve automated vulnerability scans and cut down the manual work pen testers need to do. It can also help generate exploitation code. However, AI is still far from handling the whole process, and using it raises concerns about sharing sensitive client data.
Currently, AI in pen testing is still in its early stages. “The concept of an ‘AI hacker’ has been around for a while, but it’s still a work in progress,” says Turner.
The biggest potential lies in enhancing vulnerability scans. “I’m excited about the possibility of using AI for running automated scans remotely in the future,” says Casey. “If AI can improve scanning, it will make the process faster and could even allow clients to conduct tests more frequently.”
A 2019 research paper published in the journal Computers & Electrical Engineering also points to the usefulness of AI in vulnerability tests. In the paper, titled "A Systematic Literature Review and Meta-analysis on Artificial Intelligence in Penetration Testing and Vulnerability Assessment," the authors conclude, “The application of AI in vulnerability assessment is expected to be a growing area, and its role and importance will increase as systems become more complex in our smart and connected society.”
AI could also transform penetration testing by creating self-improving systems that adapt in real time to exploit as many vulnerabilities as possible.
However, Turner emphasizes that the industry must first address the ethical and legal challenges AI presents. “We have to be cautious about what we submit to AI systems. If we share sensitive client data, we may expose it to unintended third parties, raising serious concerns. As AI evolves, I hope we see stronger safeguards to prevent misuse.”
The most efficient way to track the pen testing and compliance process
Partnering with Strike Graph as your compliance solution is the most efficient way to execute and track your pen testing. Strike Graph combines expert-led testing with automated tools to simplify every step, helping you secure systems, close vulnerabilities, and stay ahead of audits.
Strike Graph’s comprehensive penetration testing services simulate real-world attacks to help you identify and address risks before they become real threats. We provide a prioritized list of recommendations so you can resolve vulnerabilities before audits. Our AI-powered platform delivers exceptional accuracy and offers continuous monitoring to strengthen your security posture against real-world hackers.
With Strike Graph’s intuitive dashboards, you can seamlessly integrate pen test results into your compliance workflow, making tracking and reporting effortless. Our solutions support major frameworks like SOC 2, PCI DSS, and ISO 27001.
If you need the flexibility to support multiple frameworks as your company grows, Strike Graph has you covered.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)


![Blog Graphic [SEO_pen-test-phases-SG blog]](https://www.strikegraph.com/hs-fs/hubfs/Blog%20Graphic%20%5BSEO_pen-test-phases-SG%20blog%5D.webp?width=248&height=816&name=Blog%20Graphic%20%5BSEO_pen-test-phases-SG%20blog%5D.webp)

 "One of the most important questions I ask when scoping with a client is, 'What do you consider a critical finding?'" says
"One of the most important questions I ask when scoping with a client is, 'What do you consider a critical finding?'" says  "These documents outline exactly where and when we can access the client's systems," says Steven Casey,
"These documents outline exactly where and when we can access the client's systems," says Steven Casey, ![Blog Graphic [SEO_pen-test-timeline-SG blog]](https://www.strikegraph.com/hs-fs/hubfs/Blog%20Post%20Images/Blog%20Graphic%20%5BSEO_pen-test-timeline-SG%20blog%5D.webp?width=460&height=965&name=Blog%20Graphic%20%5BSEO_pen-test-timeline-SG%20blog%5D.webp)








