PCI DSS v4.0 has started taking effect, and more requirements are coming in 2025. Get ready with our comprehensive guide covering changes and new requirements. Explore our free compliance checklist and expert roadmap to implement v4.0, whether you're experienced or new to PCI DSS.
What Is PCI DSS Version 4.0?
PCI DSS version 4.0 updates the v3.2.1 standard for organizations processing or storing credit cards. It introduces new requirements and updates to address emerging security threats and provides flexible compliance options for organizations to meet PCI DSS standards.
Every three years, the Payment Card Industry Security Standards Council (PCI SSC) reviews the Payment Card Industry Data Security Standard (PCI DSS) to ensure the standards remain relevant and effective. This process helps address new threats and supports the evolving payment card landscape.
 Greig Robertson, Senior Advising Consultant at Compliance Path, emphasizes the importance of reviewing and updating PCI DSS to protect cardholder data from the latest threats. "As technology and threats evolve, it's crucial to update the standards to keep up with the times and meet security needs," he says. Robertson, a Senior IT Governance Specialist with over 10 years of experience, is well-versed in several compliance standards, including ISO 27001, SOC 2, ISO 9001, ISO 22301, and PCI DSS.
Greig Robertson, Senior Advising Consultant at Compliance Path, emphasizes the importance of reviewing and updating PCI DSS to protect cardholder data from the latest threats. "As technology and threats evolve, it's crucial to update the standards to keep up with the times and meet security needs," he says. Robertson, a Senior IT Governance Specialist with over 10 years of experience, is well-versed in several compliance standards, including ISO 27001, SOC 2, ISO 9001, ISO 22301, and PCI DSS.
To manage this review, the PCI SSC gathers feedback and insights from stakeholders, including merchants, financial institutions, and payment processors. Between v3.2.1 and v4.0, the council received over 6,000 feedback items from more than 200 companies. The PCI SSC published v4.0 in March 2022, and 13 of its requirements took effect April 1, 2024. Organizations have until 2025 to comply with the rest of the 64 new requirements. Also, in June 2024, the PCI SSC published v4.0.1, a revision to v4.0 that corrects spelling errors and refines language around some of the new requirements.
 Stephen Ferrell, CISA CRISC, and Chief Strategy Officer at Strike Graph, says that “v4.0.1 adds clarifications and guidance to v4.0 requirements but doesn’t introduce any substantive changes. The v4.0.1 updates mainly correct errors, clarify wording, and align the standard with other resources available from the PCI SSC.”
Stephen Ferrell, CISA CRISC, and Chief Strategy Officer at Strike Graph, says that “v4.0.1 adds clarifications and guidance to v4.0 requirements but doesn’t introduce any substantive changes. The v4.0.1 updates mainly correct errors, clarify wording, and align the standard with other resources available from the PCI SSC.”
The shift from v3.2.1 to v4.0.1 represents a major change for organizations across all four PCI DSS levels.
"Adapting to these new changes poses a significant challenge for both organizations new to PCI DSS and those accustomed to version 3.2.1,” Robertson says. “However, the standard exists for a very important reason — if you're handling credit cards, stringent security measures are essential to protect your customers and your organization. Following PCI DSS is the most reliable strategy to safeguard sensitive information and maintain trust with your clients and stakeholders."
Key Takeaways:
- Updated Standards: PCI DSS v4.0 updates PCI DSS v3.2.1, adding 64 new requirements to address emerging threats and provide organizations with more ways to validate compliance.
- Mandatory Deadlines: Thirteen requirements became mandatory starting April 1, 2024, with the remaining 51 becoming mandatory on April 1, 2025.
- Minor Revisions: In June 2024, the PCI SSC introduced PCI DSS v4.0.1, which includes only minor revisions and no new substantive changes from v4.0.
- Customized Approach: PCI DSS v4.0 introduces a "customized approach," allowing organizations to use innovative security controls to meet compliance requirements.
- Security Enhancements: Major security changes include more stringent requirements for multi-factor authentication, password complexity, and protection against malware.
- How to Transition: Experts recommend conducting a security gap analysis and using compliance software to automate major parts of the transition and prepare the organization.
What Are the Main Objectives of the PCI DSS v4.0 Update?
The main objective of the PCI DSS v4.0 update is to address evolving threats in the payment industry. Another objective is to provide organizations with more flexible options to meet and validate their compliance. The new standard also promotes security as an ongoing process.
Here's a summary of the four major objectives of PCI DSS v4.0, according to the PCI SSC:
- Continue to meet the security needs of the payment industry
Security practices must evolve to counter new threats to the payment card landscape. The new requirements in PCI DSS v4.0 address security vulnerabilities in v3.2.1 and target emerging threats that did not exist when the SSC introduced v3.1.
"PCI DSS v4.0 increases its focus on protecting against malware and preventing tampering with payment data,” says Ferrell. “It also introduces stricter threat monitoring requirements, provides guidance on securing cloud-based payment infrastructures, and updates cryptography standards for safeguarding payment data. All these changes are a response to new and evolving threats that threaten payment data.”
- Promote security as a continuous process
PCI DSS v4.0 adds requirements that help organizations treat security as a continuous process.
Ferrell says “continuous security” involves ongoing security monitoring, risk assessment, and control adjustments rather than only focusing on these aspects during annual PCI compliance checks. He adds, “Version 4.0.1 supports this approach by introducing new requirements for monitoring, detection, vulnerability management, and incident response.”
Robertson adds, “A continuous approach means going beyond just ticking a compliance box annually. It integrates security into daily operations and strives to exceed PCI DSS requirements.”
- Add flexibility for different compliance methodologies
Many stakeholders told the PCI SSC they wanted more options for implementing and validating their approach to meet the PCI DSS requirements. Many organizations want to use more innovative technologies that do not fit within the traditional scope of PCI DSS. The security council introduced the “customized” approach in response to this feedback.
“The customized approach allows mature organizations to design their own controls to meet PCI DSS objectives,” Ferrell says.
- Enhance validation methods
PCI DSS v4.0 improves how organizations report and monitor their compliance. Key changes include expanding documentation requirements, making every self-assessment questionnaire (SAQ) more comprehensive, and improving the clarity of the validation process. These updates ensure detailed, accurate compliance reporting and help organizations better understand and meet security standards.
High-Level Summary of New Requirements and Changes in PCI DSS v4.0
PCI DSS v4.0 introduces 64 new requirements for handling credit card transactions. The new standards improve network security and internal testing. They also tighten multi-factor authentication and offer a "customized approach" for flexibility.
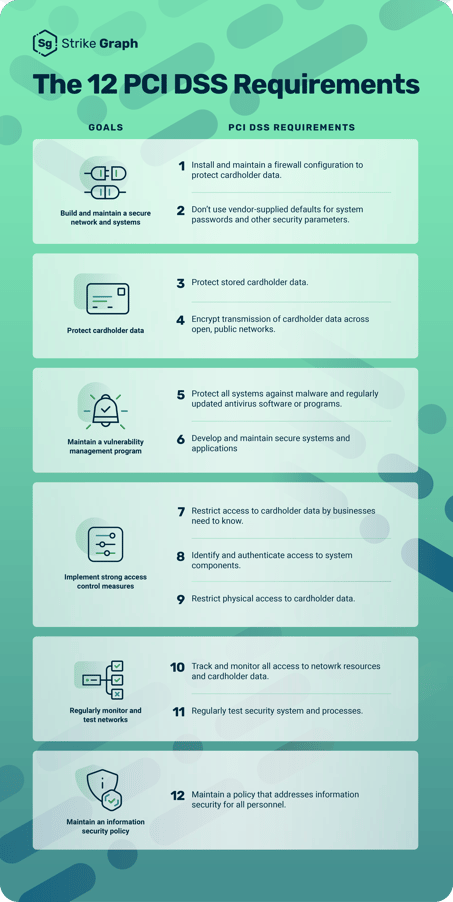
PCI DSS v4.0 does not change the 12 core requirements integral to PCI DSS. However, the new standard introduces and updates sub-requirements to address evolving threats and help organizations use more innovative technology to meet compliance.
“The most significant requirement changes revolve around authentication, passwords, MFA, and more rigorous penetration testing,” Ferrell says. “Implementing some of these requirements may be difficult for some organizations, so it’s important to start early.”
Among the 64 new requirements, PCI SSC organizations had to comply with 13 by April 1, 2024. The remaining requirements are considered best practices until March 2025. The 13 requirements already in effect focus on governance changes and documentation rather than substantive software changes.
Here’s a high-level summary of the major changes from PCI DSS v3.2.1 to v4.0. It highlights which requirements are in effect and which are upcoming. To fully understand the extent of the changes and your organization's specific requirements, review the detailed PCI DSS v4.0 documentation and consult with an expert.
- Enhanced security controls
PCI DSS v4.0 introduces more robust security controls that target new and emerging threats to the payment industry.
- Network security
v4.0 has a broader focus on network security controls to safeguard data during transmission and to prevent unauthorized access or breaches. The new v4.0 requirements extend beyond traditional firewalls and routers to include more robust and complex network security controls. The rules also help organizations adapt to new threats that can bypass traditional network security controls.
Upcoming requirements: 1.1.5 to 1.5.1
-
- Encryption and cryptography:
PCI v4.0 has more stringent password and encryption requirements. New PCI DSS v4.0 TLS (transport layer security) rules also mandate how organizations can use cryptographic keys and certificates. These rules require organizations to use stronger encryption to protect sensitive data from unauthorized users.
The major requirements are to encrypt sensitive authentication data (SAD) and certificates that verify the entities' identity when transmitting data. These certificates ensure that only trusted entities can decrypt and access cardholder data.
Upcoming requirements: 3.3.2, 3.4.2, 3.5.1.1, 3.5.1.2, 3.6.1.1, 4.2.1, 4.2.1.1
- Improved management and responsibilities
- Roles and responsibilities
A significant part of the PCI update is documenting and assigning specific roles and responsibilities for managing security controls, configurations, and activities related to data protection. These requirements try to ensure that the assigned employees are fully qualified and understand their tasks.
“Outlining the specific roles and responsibilities for various security tasks also helps PCI DSS promote security as an ongoing process,” adds Robertson. “By clarifying the specific responsibilities for each role, PCI DSS v4.0 puts an increased focus on security as a continuous process that’s integrated into the day-to-day operations of an organization, instead of only being a focus during compliance check-ins.”
Most of the 13 new requirements that took effect on April 1, 2024, center on defining roles and responsibilities.
Effective April 1, 2024: 2.1.2, 3.1.2, 4.1.2, 5.1.2, 6.1.2, 7.1.2, 8.1.2, 9.1.2, 10.1.2, 11.1.2
- Strengthening internal security and access
PCI DSS v4.0 introduces new multi-factor authentication (MFA) requirements. While version 3.2.1 listed MFA as a best practice, version 4.0 now requires it for all accounts that handle or store cardholder data.
“PCI DSS v4.0 MFA requirements make it more difficult for unauthorized entities to access an organization’s cardholder data,” says Robertson. “There are also new rules around increasing password lengths from seven to a minimum of 12 characters and changing requirements on how often organizations must review user account access privileges.”
Upcoming requirements: 7.2.4, 7.2.5, 7.2.5.1, 8.3.6, 8.4.2, 8.5.1, 8.6.1, 8.6.2, 8.6.3
- Updated testing and monitoring
- Increased penetration testing and vulnerability scans
PCI DSS v4.0 beefs up requirements to help organizations identify and address security vulnerabilities. Specifically, there is a new methodology for performing penetration tests and internal scans. These tests help determine if an unauthorized entity can access the system and find other weaknesses.
The new rules require a real, authenticated user to perform these scans under a specific methodology to ensure thorough and complete testing.
Ferrell notes that the expanded requirements around testing and monitoring may require additional work by organizations. “There are new automated log monitoring and enhanced penetration testing methodologies that may be challenging for some organizations to implement,” he says.
Upcoming requirements: 11.3.1.1, 11.3.1.2, 11.4.1, 11.4.4, 11.4.7
- Malware Protection:
Version 4.0 also improves how organizations protect against malware and phishing attacks that damage networks or trick people into giving away their personal information. PCI v4.0 introduces new tools to scan removable media, like USB drives, for malware and adds protection against phishing. The goal is to ensure that all devices connected to an organization’s network are malware-free and that employees won’t fall for phishing attacks.
Upcoming requirements: 5.3.3, 5.4.1, 11.5.1.1, 11.6.1
- Customized approach
PCI DSS v4.0 introduces a flexible way for organizations to secure their systems. The “customized approach” allows businesses to tailor their security measures while still meeting overall PCI DSS goals. “Companies can now choose the security controls that work best for them while ensuring they remain compliant,” says Robertson.
The new guidelines provide detailed instructions for the customized approach and offer supporting templates to help organizations document their controls for their assessor.
Upcoming requirements: 12.3.1, 12.3.2, Appendices D, E
Effective April 1, 2024: 12.3.1, 12.3.2
- Enhanced reporting and validation
“PCI DSS v4.0 introduces measures to improve how organizations document and communicate their compliance efforts,” says Ferrell. “For example, v4.0 introduces more granular reporting options with specific requirements. It also allows customized reporting templates, requires more detailed PCI scope descriptions, and enhances the reporting process to management. The goal is to provide greater transparency and accountability.”
PCI DSS v4.0 also introduces several changes to the report on compliance (ROC) process and the attestation of compliance (AOC) to align them with the new standard.
- Self-assessment questionnaires (SAQs)
Every SAQ has been updated to align with the expanded requirements in PCI v4.0. These updates help organizations conduct more thorough self-assessments and ensure they address all aspects of the new standard.
Upcoming requirements: Each SAQ includes updates to reflect the clarified requirements across PCI DSS v4.0
Transition Period From v3.2.1 to v4.0
The PCI Security Standards Council introduced v4.0 in 2022. Since April 1, 2024, organizations have had to comply with 11 of the v4.0 requirements. By March 31, 2025, organizations must fully comply with all 64 v4.0 requirements. This phased transition gives organizations time to implement the new standards.
“The phased rollout of v4.0 balances the need to adapt to changes while not overburdening organizations,” Ferrell says. “It provides time to roadmap their implementation and update their compliance plans for each requirement.”
Ferrell adds that the v4.01 update “doesn’t impact the phased rollout or implementation timelines. The minor clarifications in v4.0.1 can be incorporated as organizations work to adopt v4.0.”
New PCI DSS v4.0 Customized Validation Approach
PCI DSS v4.0 introduces a “customized approach” that allows organizations to use their own security controls. This change follows feedback from organizations that wanted to use custom controls. The customized approach is best for risk-mature organizations.
PCI DSS v4.0 offers organizations two methods to implement and validate their PCI DSS requirements: the “defined” approach and the “customized” approach. The defined approach continues the traditional method used in v3.2.1, where entities follow specific requirements and testing procedures to ensure compliance.
In contrast, the customized approach allows organizations to design and implement their own security controls that meet the security objectives of PCI DSS. This approach allows organizations to use innovative or more efficient security measures tailored to their specific environments. However, it requires a different validation process, including a formal assessment by a Qualified Security Assessor (QSA).
The customized approach is ideal for risk-mature organizations with advanced security measures. It allows them to leverage new security technologies and methods that might not fit within the more rigid framework of the defined approach.
“The defined approach in the PCI standard is straightforward because the PCI SSC clearly outlines their expectations and how to meet them,” Robertson says. “The customized approach, however, requires organizations to work closely with their assessor to ensure both parties understand the new controls and testing methods. While this approach offers flexibility, it demands significant effort, including targeted risk assessments and detailed discussions with an assessor. I don't see many companies choosing it due to the workload involved."
Ferrell explains, “Larger enterprises with unique payment environments often choose the customized approach. Organizations might also use it if they implement compensating controls — alternative security measures that mitigate risks when they can't meet standard PCI requirements.”
Organizations using the customized approach should consult with a QSA to validate their controls. It’s crucial to design, implement, and document the customized controls thoroughly before the assessment to help the assessor determine the appropriate testing procedures.
Implementation Steps When Upgrading From PCI DSS v3.2.1 to v4.0
Upgrading from PCI DSS v3.2.1 to v4.0 involves taking several important steps to ensure a smooth transition. First, review changes and conduct a gap analysis. Then, update your policies and documents. Also, consider whether your organization will benefit from the customized validation approach.
Here's a breakdown from Ferrell on how to upgrade from PCI DSS v3.2.1 to v4.0
- Review changes to identify gaps
First, review the new requirements, including both immediate and upcoming mandates. Conduct a gap analysis to identify where your current security measures align with v4.0 and where you need improvements.
- Prioritize high-risk gap remediation Identify high-risk areas and requirements with the earliest deadlines. Address these first to mitigate critical vulnerabilities promptly.
- Update policies, procedures, and documents Revise your organization’s policies, procedures, and documentation to reflect the new PCI DSS v4.0 requirements. Ensure all relevant materials are up to date and comply with the latest standards.
- Train your team
Provide comprehensive training for all employees involved in PCI DSS compliance. Ensure they understand the new requirements and how to implement them effectively.
- Select the right validation approach
To comply with PCI DSS v4.0, choose between the defined and customized approaches. The defined approach follows traditional methods with specific, prescriptive requirements suitable for organizations that prefer clear guidelines.
The customized approach offers flexibility, allowing organizations with mature risk management to tailor security measures to their specific needs. This approach requires thorough review and documentation to meet v4.0 standards.
When selecting an approach, consider your organization’s risk maturity, resources, and regulatory requirements. The right validation approach will help your organization achieve PCI DSS v4.0 compliance efficiently while optimizing security measures.
- Implement changes in phases during the transition period
Implement changes in phases to avoid overwhelming your team. This phased approach helps identify weaknesses early and allows for adjustments, ensuring a smoother transition.
Roadmap from PCI DSS v3.2.1 to v4.0

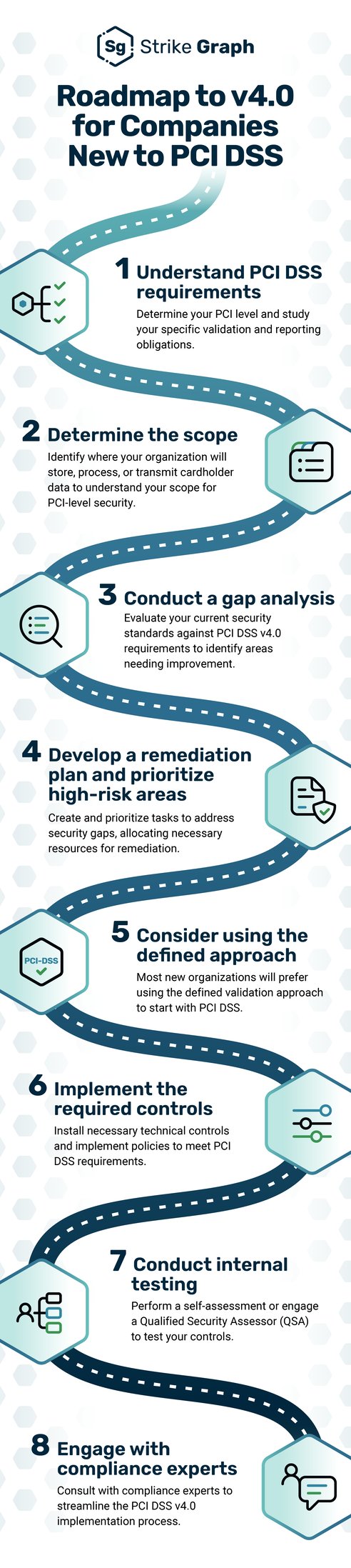
PCI DSS v4.0 Implementation Steps for Companies New to PCI DSS Compliance
Companies new to PCI DSS compliance should familiarize themselves with basic PCI DSS standards and identify their PCI level. Then, follow a structured approach similar to organizations transitioning from v3.2.1 to v4.0. Most companies new to PCI DSS will use the defined approach for v4.0.
Here’s a breakdown of the steps that companies new to PCI DSS can take to ensure they comply with v4.0.
- Understand PCI DSS requirements
The first step for any company new to PCI DSS is to determine their PCI level based on their transaction volume or anticipated transaction volume.
- Level 1: Over 6 million transactions per year
- Level 2: 1 million to 6 million transactions per year
- Level 3: 20,000 to 1 million transactions per year
- Level 4: Fewer than 20,000 transactions per year
Based on your level, you can verify the validation requirements and reporting obligations.
- Determine the scope
Identify the “cardholder data environment” (CDE) within your organization’s operations — where you store, process, or transmit cardholder data. This scope will help you understand where to implement PCI-level security standards.
- Conduct a gap analysis
Use a security gap analysis to evaluate your current security standards against PCI DSS v4.0 requirements and identify areas where your organization falls short of PCI DSS v4.0 standards.
- Develop a remediation plan and prioritize high-risk areas
Use your gap analysis to create a prioritized list of tasks to address gaps. Allocate the necessary resources to remediate these gaps.
- Consider using the defined approach
PCI DSS v4.0 offers two ways for companies to meet compliance: the customized approach or the defined approach. The defined approach offers specific, prescriptive requirements that organizations can follow.
Most experts recommend that organizations new to PCI DSS start with the defined approach. “The customized approach is focused on companies that have a very mature, risk-based approach to their security, complex IT environments, or specific security challenges,” Robertson says. “It requires extensive work from the organization to help the assessor understand their controls and testing methods. Implementing the customized approach would be very challenging for an organization new to PCI DSS.”
- Implement the required controls
Implement the policies and procedures you need to meet PCI DSS requirements. Install the necessary technical controls such as encryption, firewalls, access controls, and more.
- Conduct internal testing or schedule an assessment
Select the appropriate SAQ for your organization and perform a self-assessment to verify that your controls are effective. Engage with a Qualified Security Assessor (QSA) if you anticipate becoming a Level 1 merchant. Early testing helps identify gaps before submitting an official SAQ or undergoing a formal assessment, ensuring you monitor and maintain compliance effectively.
- Engage with compliance experts
Navigating PCI DSS compliance can be complex, especially for companies new to the standards. Engaging with compliance experts can streamline this process, ensuring you meet all requirements efficiently. Experienced professionals can guide you through each step of PCI DSS v4.0 implementation, providing tailored solutions that meet your specific needs and help you achieve and maintain compliance.
Roadmap to v4.0 for Companies New to PCI DSS
How Strike Graph Makes PCI DSS v4.0 Compliance Easier
Strike Graph transforms PCI compliance from a hassle into a smooth, automated process. Whether you're new to PCI DSS or transitioning to v4.0, Strike Graph offers customized solutions that save time and resources while keeping you current with the latest security standards.
Strike Graph’s compliance management software and expert team turn compliance challenges into strategic business strategies that improve your organization’s operations and reputation. Strike Graph’s commitment to staying up-to-date with PCI DSS and other compliance standards sets it apart from other options.
 “Keeping up with PCI DSS can be challenging for any organization,” says Michelle Strickler, Information Security and Data Privacy Compliance Strategist at Strike Graph. “Strike Graph's platform operates with the idea that addressing compliance is often unique to each organization, not a one-size-fits-all activity. With that idea in mind, we offer a full security framework that each organization can tailor to fit their unique scope and security environment."
“Keeping up with PCI DSS can be challenging for any organization,” says Michelle Strickler, Information Security and Data Privacy Compliance Strategist at Strike Graph. “Strike Graph's platform operates with the idea that addressing compliance is often unique to each organization, not a one-size-fits-all activity. With that idea in mind, we offer a full security framework that each organization can tailor to fit their unique scope and security environment."
Strickler continues, explaining how Strike Graph helps organizations switch easily from v3.2.1 to v4.0. “For example, customers bringing v3.2.1 to Strike Graph can use their old SAQ to quickly set up the requirements for version 4.0, and even v4.0.1,” she says. “Then, Strike Graph takes your existing controls and adds them to the system, so you can easily see any security gaps and assign tasks and evidence to fix them.”
Strike Graph uses the latest technology to make the compliance process easier and check your organization's controls against the latest PCI DSS standards.
“Our VerifyAI feature automatically checks your evidence against PCI criteria to see how strong your compliance is,” Strickler explains. “If the VerifyAI process doesn't approve your evidence, it tells you what's missing and suggests what you can do to fix it.”
Strike Graph is the perfect match for any organization that wants to use the new v4.0 customized approach.
“We have a mantra of risk-based, right-sized compliance,” says Strickler. “Our product lets you create customized controls and evidence that fit your unique environment, instead of being forced to use an out-of-the-box solution. You can apply your unique mitigating controls to common PCI security risks because Strike Graph allows you to create customizable controls and evidence. Also, you can deactivate elements of a framework that aren't currently relevant but might become important in the future.”
For comprehensive and future-proof PCI DSS compliance, make Strike Graph your go-to solution.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)







 “Keeping up with PCI DSS can be challenging for any organization,” says
“Keeping up with PCI DSS can be challenging for any organization,” says 


.png?width=600&height=600&name=SEO%20promo%20graphics%20(2).png)



